Cybiquity Defend is an integrated part of our managed security service, enhancing the overall experience and value we provide to our customers.
Enhance Your Security Operations with Cybiquity Defend
Unlock new defence capabilities, gain better threat visibility, and reduce complexity within your managed security service with Cybiquity Defend - our threat-informed defence platform.
Our platform provides you with the ability to review, monitor, and update your alarms in real time. It provides insight into all the analytics currently deployed in your environments (mappedto MITRE) and enables you to raise requests for information and rate tickets to provide our SOC with a view of ticket handling.
Unlocking the Benefits of Cybiquity
Reduce Complexity in MDR and SOC
Cybiquity Defend provides an easy-to-digest web portal with a clear view of the top activity, priorities, and recommendations within your MDR and SOC service.
Complete Visibility of Tickets
Immediately understand the current status of all tickets with complete transparency and a full timeline of ticket analysis.
API and Webhook Integrations
Cybiquity Defend is completely compatible with your organisation’s existing ways of working and can be directly integrated into your ITSM via API or webhook.
Deeper Phishing Insights
In Cybiquity Defend, every phishing alarm is triaged through automation with AI and sent to our analysts for a conclusion. It also provides detailed reporting on phishing within your organisation.
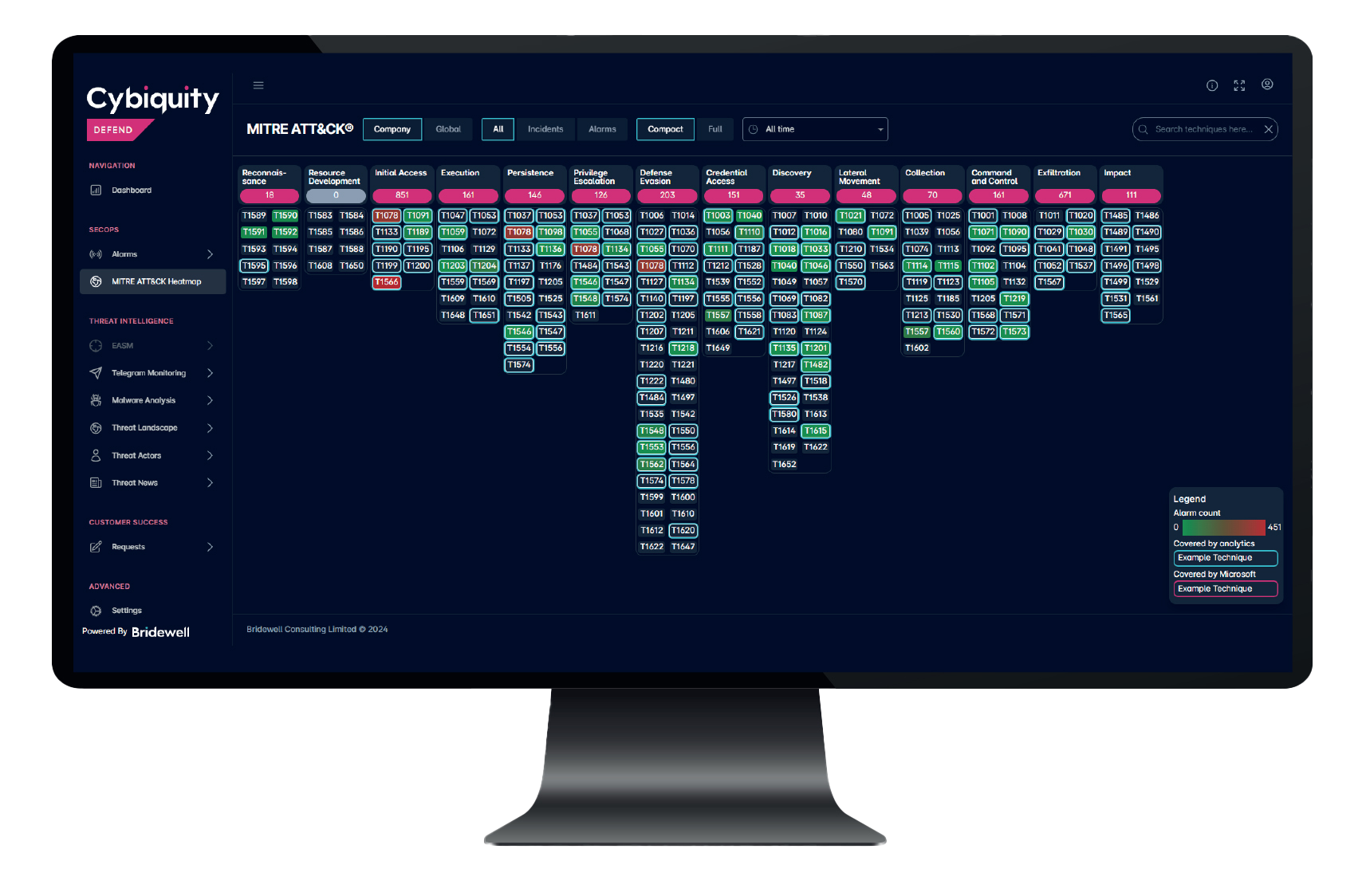
Map Alarms to MITRE Framework
All alarms within Cybiquity Defend are mapped to the MITRE framework, including a heatmap to show which attack vectors are most prominent within your organisation.
Dynamic Sandbox Capability
Whenever a piece of malware is prevented from executing, Cybiquity Defend will launch a dynamic sandbox to detonate it to understand the TTPs it uses. This insight is linked to the ongoing malware research of our Cyber Threat Intelligence (CTI) team.
Threat Intelligence Database
Cybiquity Defend provides you with complete access to our threat intelligence database, including a snapshot view of the current threat landscape and the top nation state actors, cyber criminal groups, TTPs, IoCs, and malware families.
Breach and Attack Simulation
Cybiquity Defend delivers automated testing based upon specific threat scenarios.
Start your Cybiquity Journey
Speak with one of our consultants to see how we can support your organisation with it’s cloud environments.

How it Works

Real-Time Alarms and ITSM Integration with Cybiquity Defend
The platform will enable you to review and action alarms in real time, enabling faster and more effective ways of collaborating with our SOC. Cybiquity Defend also enables you to configure intergration with your ITSM tooling.
Cybiquity Defend: Real-Time Threat Detection and Response
By both generating and consuming threat intelligence, and using models such as the Mitre ATT&CK framework, Cybiquity Defend highlights the potential and actual threats to your organisation, whilst extracting real-time actionable intelligence to prevent, detect and respond to rapidly emerging threats.
Why Us?
Awards
Our team have won numerous industry awards, including 'Cyber Business of the Year' at the National Cyber Awards 2024 and 'Best Cyber Security Company of the Year' at the Cyber Security Awards 2023.
Certifications
Our people and services are highly accredited by leading industry bodies including CREST, the NCSC, and more. Our SOC holds extensive accreditations from CREST (including for CSIR and SOC2) and works closely with our cyber consultancy services.
Partnerships
As a Microsoft Partner, we also hold advanced specialisms in Cloud Security and Threat Protection. We’ve also implemented some of the UK’s largest deployments of the Microsoft Security stack, inc. Sentinel, Defender, Purview and more.
