This article presents a checklist of factors for avoiding common pitfalls in establishing a ZT programme, and lists lesser-known benefits and risks.
According to a recent survey1, 83% of UK organisations are planning (or are in the midst of planning) a Zero Trust (ZT)2 programme. This article presents a checklist of factors for avoiding common pitfalls in establishing a ZT programme, and lists lesser-known benefits and risks. By following this guidance, you can better understand when, how, where and why to implement ZT and avoid your initiative joining the 70% of digital transformations estimated to end in failure.3
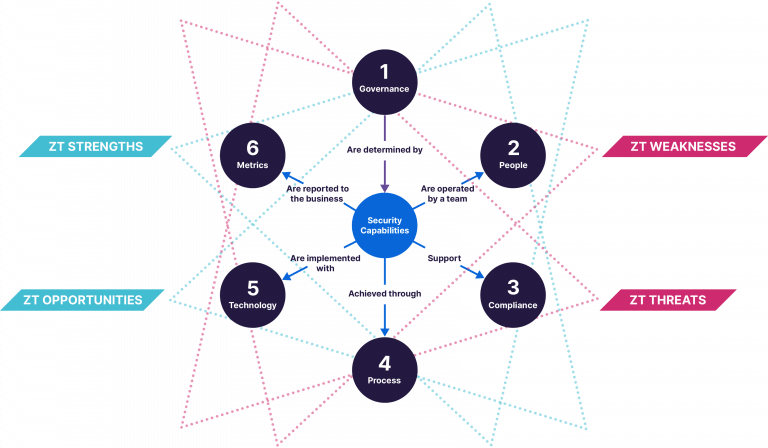
Given the extensive, solution-agnostic guidance available for implementing ZT, such as from the National Cyber Security Centre4, this article will instead look specifically at the components of people, process, technology, governance, compliance and metrics and how they all contribute to the operating model of a healthy security function. For each component, we ‘shine a light’ on the positive and negative impacts a ZT programme may introduce.
This table provides an overview of the key strengths, opportunities, weaknesses and threats. For more information on any of these points, please see below. (Click on a specific business area to jump to the relevant section.)
Business Area | Strength | Opportunity | Weakness | Threat |
|---|---|---|---|---|
Governance | • Simple story • Buy in/ hype among stakeholders | • Risk-based prioritization • OpEx model • Strong ROI | • Lack of sponsor • Not a silver bullet • False sense of security • Fragmented tools | • Attention deficit • Vendor lock in |
People | • User centric • UX focus | • Fix excessive privileges • Identity based approach • Labour savings | • Resistance to change • Lack of expertise | • Training costs • Dependence on partner • Default deny versus culture • Delivery team not empowered |
Compliance | • Reduce risk • Uniformity • Continuous compliance • Fine-grained | • A differentiator for suppliers | • Loss of firewalls, DMZs. | • Poor data classification • Future regulatory risk |
Process | • Consistent controls • Benefits process of defence | • Simplify access control • Can coexist with existing processes | • Hybrid mode • Unsupported subset of private applications • Needs detection and response maturity | • Project Management errors. • Aggressive rip and replace • Friction in continuous verification • Underestimating integration • Poor exception management |
Technology | • Tried and tested. • Enables CTO priorities • Infrastructure savings | • Microsegmentation possible • Retire some networks • Use existing components | • Layer 7 implementation versus L3. • ZT depends on individual resources that communicate. • May need to keep VPN. • Large implicit trust zones | • Implementation could be a mis-match • Distraction from other risk vectors – phishing, app vulnerabilities • Retire too much network |
Metrics | • Control and data plane logs • Host based monitoring | • Improvement on MTTR, MTTD and security KPIs • Real time diagnostics | • Lost Network visibility | • Inappropriate telemetry for decisions |
Governance
Strengths
ZT has captured imaginations and tells a simple (but not easy) story. This is a fortunate occasion where the hype around an approach can actually deliver significant benefit to the business.
Stakeholders can buy into ZT and are encouraged by the social proof of companies like Google and Microsoft who have paved the way with declining costs and the promise of savings.
Opportunities
While there is early momentum for the ZT mandate, IT and security leadership can achieve better results by prioritising particular projects in the initiative that will be deliver the best results, for example: Zero Trust Network Access (ZTNA), Cloud Access Security Broke (CASB), Secure Web Gateway (SWG), Data Loss Prevention (DLP), etc.5
ZT can be procured on both a consumption model or in lump sums with a managed provider. Both are likely better than capacity-based CapEx on security appliances and licenses.
Forrester research reported 92% annual return on investment from Microsoft’s ZT solutions (i.e. organisations investing in these solutions can achieve payback within a year in labour, incidents and management savings).6
Weaknesses
As a paradigm shift, ZT will involve many internal stakeholders and silos, and could fail without suitable sponsorship in an organisation with change fatigue or dysfunction.
Many decision makers will bring preconceptions that may need to be challenged. ZT cannot be treated as a silver bullet but instead as a complement to other principles like Least Privilege and Separation of Duties.
Implementing Zero Trust could bring a false sense of security. For example, it is a good approach for BYOD but is not perfect. For example, it has imperfect visibility into devices when they are disconnected.
The organisation will over time build a suite of ZT security capabilities. If not properly coordinated, this could be fragmented across many suppliers and solutions, with misaligned management and policies.
Threats
Attention Deficit: This programme will likely span more than one technology refresh cycle (3-4 years) so it must compete for priority at corporate level and demonstrate ongoing Return on Investment from the start.
There is a risk of vendor lock-in by consolidating so many areas of access control to a single supplier.
People
Strengths
Zero Trust has thus far concentrated on access control for humans and has been user centric. For example, for Work From Home. Users are more supportive when a security solution is designed around their use cases and makes their life easier (e.g. Single Sign-On). Products are also well-suited to modern challenges of business partners and contractors.
The improvements to user experience of ZT Network Access versus an always-on VPN are considerable, as is implementing Single Sign-On.
Opportunities
Zero trust presents a change to address stubborn problems of excessive privileges
Indeed, it is possible to make identities the heart of a zero trust strategy by using Identity Governance and Administration (IGA) and PAM (as described by the ID Security Alliance).7
Organisations can expect labour efficiencies for network, helpdesk and security teams in the double digits of percent.
Weaknesses
IT staff and users may express a resistance to change.
Part of this can be a lack of expertise in the organisation (and indeed the whole industry).
Threats
Zero Trust has a learning curve and there is a training overhead for staff. Larger organisations also typically bring in a delivery partner to assist, which makes it important to choose the right people.
Rolling out default deny in earnest may raise complaints from sysadmins or others who have to change their previous way of working.
The initiative needs to be empowered to take decisions and address complaints like these, ideally at the feature-team level (as described by Microsoft).8
Compliance
Strengths
Zero trust organisations reduce their risk exposure by up to 54%.9 They can also establish consistent baselines and uniform access across disparate systems.10
Zero trust can deliver continuous compliance through posture checks and monitoring that support continuous trust verification.
Fine grained access and segmentation can reduce the scope for compliance and fix compliance headaches like external collaboration.
Opportunities
Suppliers that implement zero trust can provide a level of comfort and differentiate themselves to procurement teams that are increasingly concerned with their partners’ security risk profile. Partners accounted for 60% of system intrusions in the latest Verizon Data Breach Investigations Report.11
Weaknesses
Certain standards and auditors may not accept the removal of traditional controls like multiple firewalls and de-militarised zones.
Threats
Classifying data is a vital early step so that zero trust can align its priorities. If there is no internal compliance with data classification, zero trust will lose its focus.
Regulatory change is always a threat. Thus far legislators and regulators have been supportive.12 In future, some may take an opinionated view that does not support some implementations.
Process
Strengths
This initiative can deliver consistent, dynamic access control policies and process everywhere, enforcing least privilege access to critical resources, potentially via a single policy engine and gateway.
It benefits the entire process of defending the enterprise, especially across Harden, Detect, Isolate, Deceive and Evict (MITRE D3FEND).13
Opportunities
Done well, this initiative can simplify access to resources and deliver economies in infrastructure, IT admin and security management.
In many instances, existing business and technology processes are compatible with zero trust and do not need complete replacement from scratch.
Weaknesses
Large and enterprise scale organisations will need to work in hybrid mode with both perimeter and ZT security in effect for a period of switchover (which will usually take months).
Certain business processes are outside the technical scope of some Zero Trust solutions: cloud-native and SaaS applications, until a CASB-like solution is used, or server-initiated apps.
Insufficiently mature detection and response processes quickly suffer from many false positives among the logs.
Threats
Mismanagement of the delivery programme is a threat. For example, designing the wrong rollout rings, deploying UX components before infrastructure, or lack of accountability, cross function collaboration and employee engagement in the Project / Programme Management Office.
Programmes that rip and replace too aggressively are likely to fail – the change should be incremental. In their case study, LogRhythm took 4 years to increment their Zero Trust capability, making efficiencies with projects like GDPR.14
Technology
Strengths
The leading products supporting zero trust are tried and tested and their vendors are well established.
Zero Trust aligns well with recent trends of CTO focus – Virtual networking, SDWAN and remote working at the edge.
By enabling both remote users and server-to-server traffic without routing via an HQ circuit, it can reduce the spend on communications infrastructure (which accounts for a quarter of IT spend).15 It also helps with reducing the stack of agents and software.
Opportunities
Application-based access control can unlock microsegmentation which has historically been avoided because of the firewall rule complexity.
The organisation can choose to stop maintaining their own MPLS, WANs, WiFi, and can securely use new communications technology like 5G.
Existing vendors and product suites may be able to deliver much of ZT without new spend, for instance by orchestrating configuration management and host firewalls.16
Weaknesses
In contrast to a software defined perimeter implementation, an application layer implementation of ZT could be more susceptible to vulnerabilities at layers 3 to 6: Transport Layer Security (TLS) vulnerabilities and attacks on session startup.17
ZT requires individual resources that can communicate with a gateway. This excludes some legacy applications or large in-app landscapes like ERP.
For such edge cases, the existing VPN solution may need to persist.
ZT can create zones of resources and these zones (e.g. enclaves) have implicit trust, so must be kept as small as possible.
Threats
Choosing the wrong implementation could result in a mismatch with your infrastructure. For example, making a vendor’s firewalls the policy enforcement point rather than an agent or the vendor cloud.
Some services will need special handling, like legacy applications that do not support modern authentication.
ZT focus could distract from other key vectors of security risk such as phishing or application vulnerabilities (CIS Controls 16, 9).18
Retiring the network is possible but could be excessive if some links are essential for SLA guarantees and Quality of Service.
Metrics
Strengths
Zero Trust can reduce the panes of glass in use and produce meaningful telemetry for IT and security operations, available from on-host agents and the APIs.
These include both control plane and data plane logs in the same place, synchronized and sometimes correlated.
Opportunities
The level of security visibility is usually improved when a single vendor has sight of the source endpoint, cloud gateway / proxy and destination resource and that feed is well-monitored. Accordingly, mean time to detect and respond typically fall due to a simpler ecosystem.
With continuous verification as a founding principle, vendors can support (near) real time diagnostics by default.
Weaknesses
Network visibility and content inspection are impaired if end-to-end encryption is used without TLS interception. Useful VPN logs are also reduced or lost.
Threats
Decisions about granting access are only as good as the contextual data they are based on. Using too little or inappropriate telemetry can skew these decisions.
Zero trust is absolutely a net positive for security posture as a whole. However, there are margins of error between a good implementation and a great one, as well as the possibility of creating a sub-optimal one. This high-level list of factors across the security operating model should provide some new considerations for your Zero Trust programme and security function so you can realise the opportunities available and address the threats.
References
The US National Institute for Standards and Technology definition is: ‘Zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources.’ https://csrc.nist.gov/publications/detail/sp/800-207/final
https://www.ncsc.gov.uk/blog-post/zero-trust-is-it-right-for-me
Zero Trust Network Access, Cloud Access Security Broker, Secure Web Gateway, Data Loss Prevention.
https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RWRIEi?culture=en-us&country=US
https://www.microsoft.com/en-us/insidetrack/lessons-learned-in-engineering-zero-trust-networking
ibid.
https://www.verizon.com/business/en-gb/resources/reports/dbir/2022/results-and-analysis-intro-to-patterns/ , especially the SolarWinds incident.
See for example White House Executive Order No. 14208 https://www.whitehouse.gov/briefing-room/presidential-actions/2021/05/12/executive-order-on-improving-the-nations-cybersecurity/
$1.4tn of $4.2tn globally: https://www.gartner.com/en/newsroom/press-releases/2022-04-06-gartner-forecasts-worldwide-it-spending-to-reach-4-point-four-trillion-in-2022
https://logrhythm.com/how-to-build-a-zero-trust-ecosystem/
Gilman, E and Barth, D: Zero Trust Networks https://www.oreilly.com/library/view/zero-trust-networks/9781491962183/ Ch.9, Realising Zero Trust
Cloud Security Alliance, Software-Defined Perimeter (SDP) and Zero Trust https://cloudsecurityalliance.org/artifacts/software-defined-perimeter-and-zero-trust/
https://www.cisecurity.org/controls/cis-controls-list




