The objective of a security operations centre is to prevent, detect, investigate, and respond to cyber security attacks and they do so with mixed results.
Security operations focusing on cyber defence or blue team tactics need several tools to successfully achieve their objective and with the number of tools and vendors usually within operation, deploying a Zero Trust security framework to support a modern, digital business is an impossible task.
The key tools that enable visibility and the ability to prevent, detect, investigate, and respond are conceptually simple. They need the ability to be able to have a single view, analysis, correlation, and real-time alerting of activities across all technology and platforms, not just security devices. They need to be able to respond in near real-time to threats and alerts to investigate and contain or disrupt potentially disruptive activity and lastly, there needs to be an ability to automate some of the security activities to reduce the response times and noise seen by skilled analysts.
The challenge is that current tooling does not really allow for this to happen effectively. Many security vendors have API’s available, and some vendors now have Security Orchestration, Automation and Response (SOAR) tools that are starting to become the glue between vendors and products. However, the overhead cost of owning and managing a wide number of vendors and devices, plus the integrations continue to push the cost of delivering an effective security operation upwards, making an ROI hard to achieve or investment hard to approve.
As an example, let us review the illustration below.
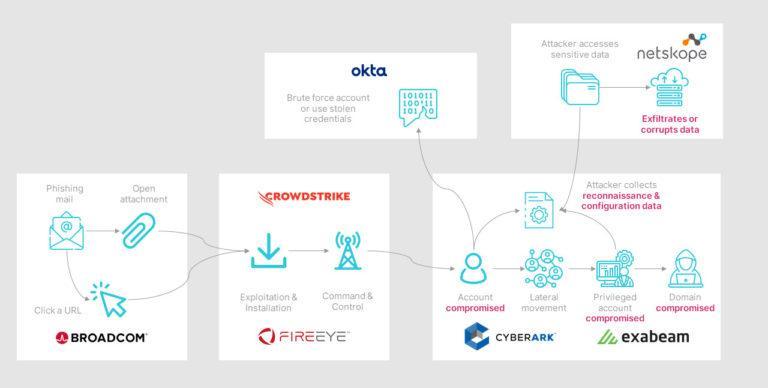
In this attack, a desktop user accidentally opens an email containing malware that leads to wider lateral movement, escalation, and the successful exfiltration of data. The attack chain is covered by security technology comprising of seven vendors that share no information or context of what has happened elsewhere in the kill chain. The complexity and lack of cohesion results in a delay in the detection time and a lack of automated response. Having to perform investigations and forensics across the entire stack is manual, time-consuming and most importantly, it continues to be damaging until disruption and containment is complete.
The Microsoft Security Architecture
The benefit of a single vendor architecture is that all of that “stitching” via API is usually already done, reducing the management and development overhead. Using fewer or a single vendor allows for further cost savings through vendor consolidation.
So, what if you were able to get the tools and capabilities that can be easily stitched together, deliver the ability to prevent and respond to threats and have the widest coverage of extended detection and response (XDR) at no extra license cost? Well, this is what Microsoft is offering with the inclusion of the Microsoft Defender XDR product suite within its Microsoft 365 licensing.
To bring it all together and really feed the security operations is the Azure Sentinel. Azure Sentinel is a cloud-native security information and event manager (SIEM) platform that uses built-in AI to help analyse large volumes of data across an organisation at rapid speed. What is more, it has out-of-the-box connectivity that allows you to stitch all those tools into a single pane of glass for a security operation to analyse, respond and automate activity against.
What is Microsoft Defender XDR?
We talked about XDR more widely in a previous blog post about "How Does XDR Fuel the Modern SOC?", but Microsoft Defender XDR was announced at Microsoft Ignite in 2020 as the unified cyber defence platform that encompasses the entire Microsoft security architecture, that is over 40 security tools. It includes all the elements available in the E5 (or A5 for educational users) licensing and what was formerly the Azure Security Centre.
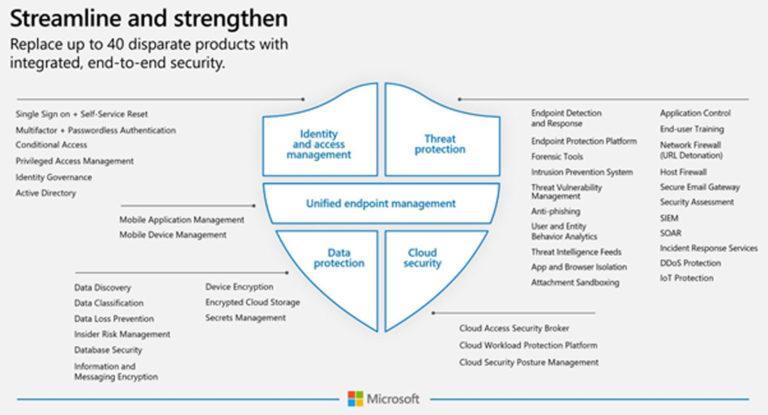
The top-level products that comprise Microsoft Defender XDR include:
- Microsoft 365 Defender (formerly Microsoft Threat Protection)
- Azure Active Directory
- Microsoft Cloud App Security
- Microsoft Defender for Endpoints (formerly Microsoft Defender ATP)
- Microsoft Defender for Identity (formerly Azure ATP)
- Microsoft Defender for Office 365 (formerly Office 365 ATP)
- Microsoft Endpoint Manager
- Azure Defender
- Azure Defender for Servers (formerly Azure Security Center Standard)
- Azure Defender for IoT (formerly ASC for IoT)
- Azure Defender for SQL (formerly ATP for SQL)
Many of the XDR products are recognised as leaders by Gartner, with five of the solutions featuring on Gartner Magic Quadrants in 2020. A feat the competition is struggling to keep pace with. The toolset and capabilities support cloud-native and hybrid infrastructures ensuring consistency of security, regardless of the workload or technology location. In fact, using services such as Azure Arc, you can manage services anywhere, including AWS and GCP and provide oversight from Azure Defender.
So, how do we bring all this together for visibility and incident management across the Defender XDR products, but just as importantly, get visibility into the events received from the wider architecture and systems? This is where Azure Sentinel comes into play.
What is Azure Sentinel?
As defined earlier, Azure Sentinel is a cloud-native SIEM that leverages the scale and power of Microsoft to deliver a high performing analytical tool that uses built-in AI to analyse data from across the organisation.
Yes, it’s a SIEM. Yes, it competes with the other large players in the SIEM market, but the cloud-native architecture giving limitless cloud speed and scale and the design of a solution that is designed to address the challenges facing a SOC make it a leader amongst its peers. However, it did not appear on the Gartner Magic Quadrant in 2020 due to how new it was (GA in Sep 2019). At Bridewell, we fully anticipate that it will make an appearance in the soon-to-be released 2021 MQ, extending Microsoft’s leadership and vision for cyber security.
Couple the SIEM platform with AI that can analyse over 250,000,000 monthly users and activity to identify malicious traffic across its entire user base, and you have a highly capable SIEM.
Not just a SIEM
But we’re not done there. Within the Sentinel SIEM is an integrated SOAR capability. This is not another bolt on or integration, it’s native within the tool. Using the SOAR, you can automate the enrichment of incident data, notify analysts of incidents via email, teams, SMS and ITMS integrations. Even better, you can take automated steps to respond to alerts in near real-time. This is all regardless of the data source and the security tool that needs the response. Granted, it’s much simpler and easier when integrated into the Defender XDR suite of tools. These can be further enhanced and developed using Playbooks which can leverage Logic Apps for great extensibility.
Using the incident management capability within Sentinel, your analysts can investigate, document, note, respond to and close incidents directly within the tool, delivering an instant security incident management tool with the power to drive performance measurement. KPI’s such as Mean Time to Triage and Mean Time to Respond can be tracked within Azure Sentinel so that you can continue to measure your performance and improvements of the security operation over time.
Lastly, all that data from such a wide set of data sources readily enables the development of threat hunting as a practice, searching for activity that is persistent and able to evade other defence tactics. The power of the query language enables results of complex queries over large data sets to be returned instantly in seconds where traditional solutions allowed you to make a cup of tea before getting the answer to a single query. In fact, Microsoft has ready-made threat hunting queries that enable you to hit the ground running and leverage the scale and intelligence of Microsoft’s security analysts.
Integrated Detection and Response
Now we understand XDR and Sentinel, let us replay the earlier example but this time, under the Microsoft security architecture.
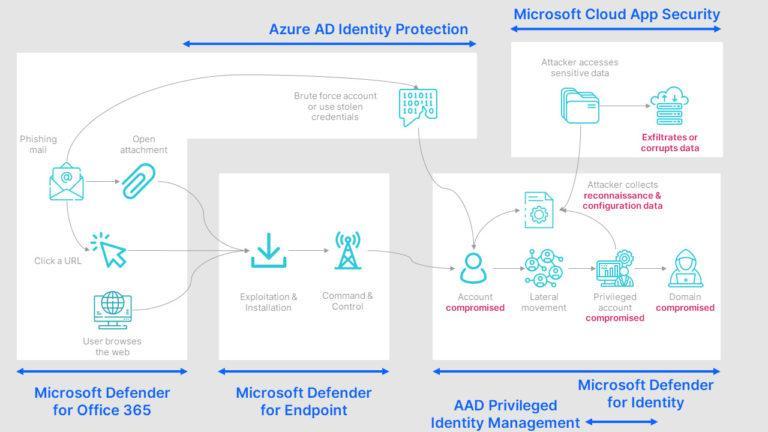
Due to the integrations and context sharing between the XDR products, each product enhances the fidelity of any previous alert and enriches the security incident that is generated within Azure Sentinel so that you have sight of the entire attack chain from a single view.
Touching again on SOAR, using the capabilities inherent in Azure Sentinel that integrates with Defender XDR you can automate the response which is triggered in seconds and not minutes or hours. The automation could for example disrupt the activities by resetting and disabling accounts, removing malicious emails from inboxes, and blocking traffic on the endpoint, all without user intervention.
A leading cloud-native SIEM, for free
Lastly, let us look at the cost of Sentinel, well the tool itself is free. That’s right, all that capability, power and scale for free. What you do have to pay for is the data that you ingest into Azure Sentinel on a per GB per month scale for as little as £0.78 per day. However, Microsoft does not charge you for data that you are pulling in from its other tools within the defender suite such as O365 audit logs, Azure activity logs and Defender (formerly Threat Protection) protection logs.
So, the costs come from systems such as application, server and network information that sits outside of these platforms, which can be tuned to send only relevant information.
As part of the MDR service from Bridewell, we actively manage the ingestion costs and make recommendations and tune out event noise that is driving up the cost but not adding to the fidelity of alerts.
The performance and value increase of a Microsoft Security Operation
We have walked through a common attack scenario and seen how effectively the Microsoft Security Architecture would deal with the scenario given the end-to-end coverage of the kill chain. With the average cost of a breach being $3.86 million and on average 280 dates to detect and contain a breach according to the IBM 2020 Cost of a Data Breach Report, the value of adopting such an integrated and capable security architecture is great.
From a performance perspective, we can move to a position to respond within seconds automatically, or fire off alerts for analysts to respond to in minutes. Not only that, but it is measurable within the tool to monitor performance over time.
So, where you are already on the E5 journey (including elements such as E5 Security or Windows 10 E5, not just M365 E5), then you can leverage all the protections of Defender XDR capabilities for no additional cost. Realistically, stepping up from an E3 license to E3 + E5 Security which is our minimum recommendation will have a circa 30% uplift on those users being protected. Although, you can bolt on some individual components of the Microsoft 365 Defender at a lower incremental cost.
The key here will be to review your existing vendors and overlapping products and understand what their cost is to fuel an internal ROI discussion to support your move to the Microsoft security stack.
When measuring the ROI of the Azure Sentinel, Forrester measures a three-year ROI of 201% and a payback within six months. Most of that cost comes in the form of deployment services and the resource and skills needed to get up to speed and maintain the solution. So, the evident value of working with a partner such as Bridewell for the delivery under a managed service agreement increases the ROI by over 20%.
I think it is fair to say that Microsoft Sentinel and Defender XDR combined undoubtedly improves the performance of security operations and given the integrated capabilities within existing Microsoft licensing structures, the ROI is high.





