If you’re looking to more effectively triage, investigate, and respond to attacks in your environments, you may have considered deploying Security Copilot. This generative AI tool, launched earlier this year by Microsoft, promises to strengthen your security team’s expertise, help you outpace adversaries, and generate key insights from vast data signals.
Given these capabilities, many organisations are already looking to deploy Security Copilot in their own environments. To help you plan your own deployment, this blog will cover how Security Copilot works, how you should prepare to deploy it, and how you can maximise value from this tool.
For more on this topic, we also recommend watching our Security Copilot webinar webinar on-demand.
Why Deploy Security Copilot?
50% of all UK businesses have a basic cyber security skills gap, according to research from the Department for Science, Innovation and Technology. This shortfall in skills makes it hard for defenders to ensure they have enough people in place to respond to a growing volume of incidents, alarms, and events.
At the same time, we are also seeing the volume and sophistication of threats increasing. Microsoft research also highlights that there are around 4,000 password attacks per second and the mean time for an attacker to access your private data following a successful phishing email is only 72 minutes.
Given these challenges, our goal as defenders should be to reduce the mean time to detect and respond and contain incidents sooner. This is where Security Copilot can help, empowering in-house and hybrid security operations teams to protect at the speed and scale of AI.
How Does Security Copilot Work?
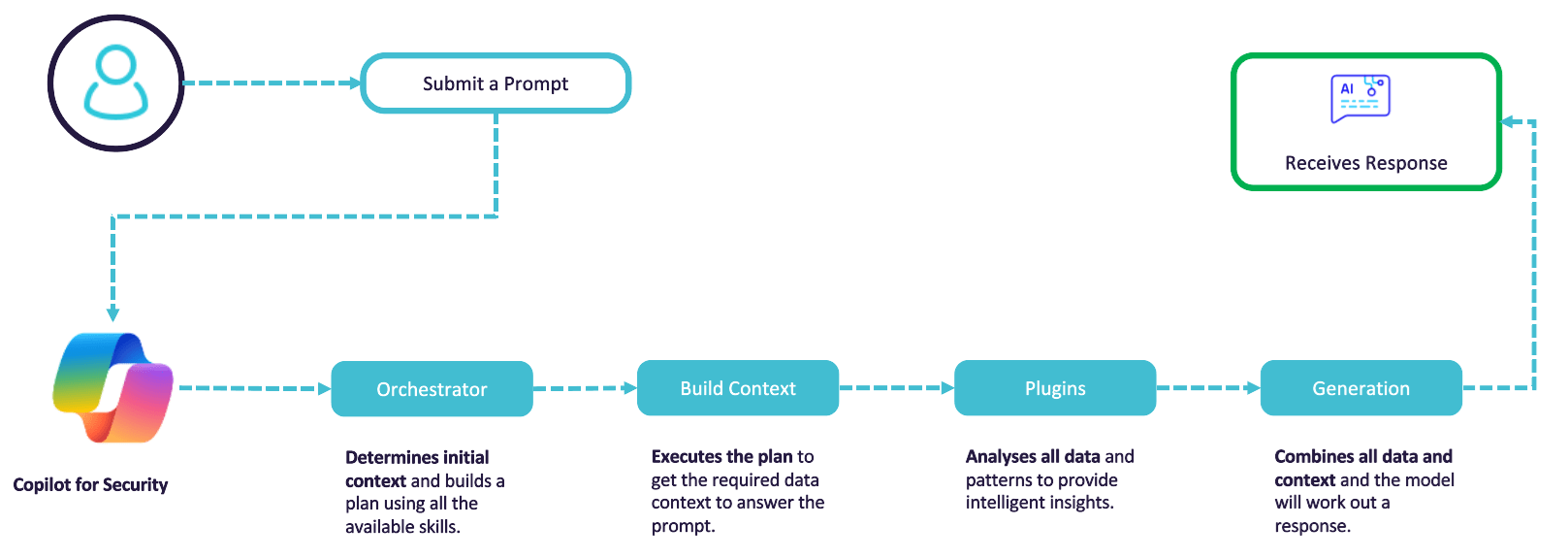
To ensure the most effective deployment of Security Copilot, it is first important to understand how it works. Security Copilot works much like any other GPT capability. You write a prompt and Copilot will then determine initial context, building a plan to gather the necessary data to answer your prompt based on the skills, integrations, and technologies you have available.
From here, Security Copilot will execute your queries, which is where your integrations with other Microsoft and third-party technologies are essential to informing Copilot with the right data. This data is then analysed, with Copilot generating content based on your original request and the data it has access to.
With this process in mind, your integrations with other Microsoft Security technologies are invaluable to providing Copilot with more insight, enabling better responses to your queries. Security Copilot comes out-of-the-box with strong integrations to the rest of the Microsoft Security ecosystem – including Defender, Sentinel, Purview, Priva, Entra and Intune. Depending on your integrations, this can extend the value of Security Copilot beyond security operations and into areas like device compliance, ID, and threat intelligence.
Security Copilot also allows you to integrate with third-party products. There is already an extensive catalogue of out-of-the-box integrations with third-party vendors, but it is also possible to build you own. This means that if, like many organisations, you don’t run purely on Microsoft, you will still be able to gain value from these products within Copilot. This is particularly useful for organisations with extensive operational technology (OT) or ICS environments.
How to Get the Most out of Security Copilot
Integrate with Other Microsoft Security Products
Given that Security Copilot directly benefits from integration with wider tools, especially the Microsoft security stack, consolidating your investments in the E5 product suite ahead of your deployment can be a good place to start. It is also worth maximising your coverage with Microsoft Defender, whether that’s Cloud, Endpoint, or Identity.
Likewise, you can benefit from making use of Entra for identity, Intune for device configuration, and Purview for data loss prevention and privacy. In doing so, you will be able to maximise the use of all these technologies and build a strong foundation from which Copilot can give you the best contextual information about your organisation and act as an effective assistant for your security team.
How to Prompt Security Copilot
Another area you can focus on to gain more value from Security Copilot is in improving how you craft prompts. As with any GPT, submitting well-crafted prompts will help you get the outputs you need faster. In short, you should:
- Be clear in your direction and what you want to achieve
- Supply necessary context to help Copilot narrow down where it is looking for data
- Set clear expectations of which audience and format you want the output to be tailored for
- Provide a source by suppling any relevant sources or plug-ins
- Directly address Copilot in the second person (i.e. talk to Copilot like a real assistant)
You may also want to focus on developing promptbooks. These are powerful assets for streamlining investigation when it comes to multi-step tasks. These can be designed to run with a single click, saving your security team valuable time. Copilot comes with many standard promptbooks for common task flows, but you also have the option to create and edit custom promptbooks.
For help building custom promptbooks or understanding best practice for prompting, see our Security Copilot Prompt Engineering service.
How to Deploy Security Copilot
For many organisations, working with a Microsoft partner can help them get more value out of their Copilot deployment. Not only will their experience with the wider Microsoft security stack help you integrate Copilot with the rest of your security ecosystem, a partner can also support with crafting better prompts or developing promptbooks.
As one of the earliest partners chosen for the Microsoft Security Copilot Private Partner Preview, and bringing years of experience deploying Sentinel and Defender for some of the UK’s largest CNI organisations, our Microsoft specialists are well-positioned to support these activities and help you get the most value from Security Copilot.





