The Cyber Assessment Framework (CAF) is an increasingly important cyber security framework for organisations to understand – both as a means of driving cyber security improvements and of achieving regulatory compliance.
This blog provides an overview of how the CAF is structured and how it is used and applied. This is the second part of our CAF Connect series, an ongoing series of content and events where our experts share their knowledge and advice on the framework to help you achieve compliance.
What is the Cyber Asessment Framework (CAF)?
The CAF is an outcome-focused framework, designed to be used in both self-assessment and regulatory assessment capacities by Competent Authorities. The ultimate aim of the framework is to assess if the strength of your cyber security measures is proportionate to the security risks facing your organisation’s safe and secure operations, as well as the operations of all broader functions or services you support.
As a self-assessment tool, the CAF also allows organisations to evaluate and improve their cyber resilience, thereby effectively managing security risks and protecting essential functions against adverse cyber events. More specifically, the CAF looks at how capable your organisation is at managing security risks efficiently, detecting cyber security events, and responding to cyber security incidents
The Cyber Assessment Framework (CAF) and the Network and Information Systems (NIS) Regulations.
As a framework, the CAF is important to many organisations who are subject to the Network and Information Systems (NIS) Regulations. The National Cyber Security Center (NCSC), the UK Government’s technical security arm and part of the Government Communications Headquarters (GCHQ), have produced the CAF to ensure a degree of consistency between the different sectors regulated under the NIS Regulations.
How is the CAF Structured?
The foundation of the CAF is its Principles, which are grouped under four overarching Objectives. Each Principle is supported by a series of more granular Contributing Outcomes, which, in turn, are supported by a series of Indicators of Good Practice (IGPs).
If this seems confusing at first glance, don’t worry – it can take some time to understand how the Objectives, Principles, Contributing Outcomes, and IGPs work together! We’ve broken each of these down to help fill in the gaps.
The CAF Objectives
The CAF’s four Objectives are:
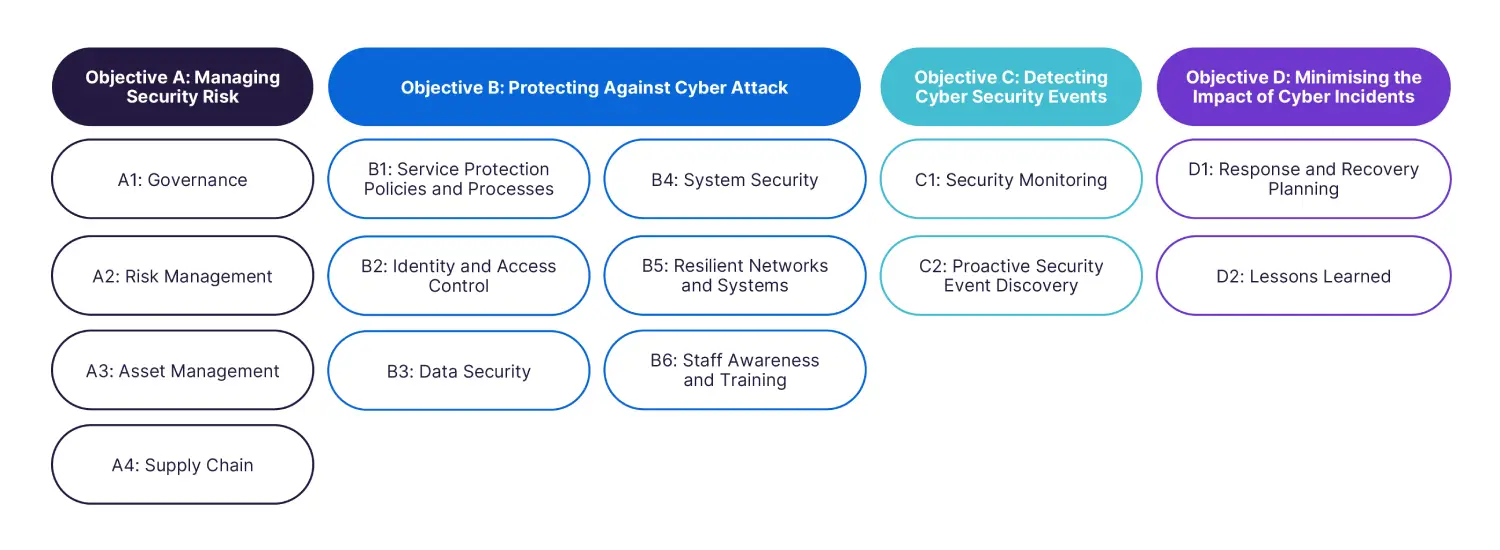
Objective A: Managing Security Risk.
Objective B: Protecting Against Cyber Attack.
Objective C: Detecting Cyber Security Events.
Objective D: Minimising the Impact of Cyber Security Incidents.
Whilst the Objectives are distinct, they are also integrated and mutually supporting. Specific areas of security cannot be effective without both other related areas and the integration with them also being effective. An obvious example is that technical controls to protect against cyber attack (Objective B), however strong they are inherently, are unlikely to be effective in their implementation without strong governance and processes for managing security risk (Objective A).
In this vein, Objectives A and D broadly contain requirements which are aimed at an entire organisation, such as its cyber risk management or incident response functions. Assessing performance against these Objectives can typically be done once across the organisation, with some exceptions.
Objectives B and C broadly contain requirements which are aimed at individual systems, such as an organisation’s control system or its forecasting tooling. Assessments against these Objectives, in most cases, require individual assessments to be conducted against each of an organisation’s in-scope systems.
CAF Principles
At the heart of the CAF are the NCSC’s 14 Cyber Security and Resilience Principles, which break down each of the four Objectives into a collection of outcome-focussed statements, under which more granular assessment requirements (Contributing Outcomes and IGPs) are grouped.
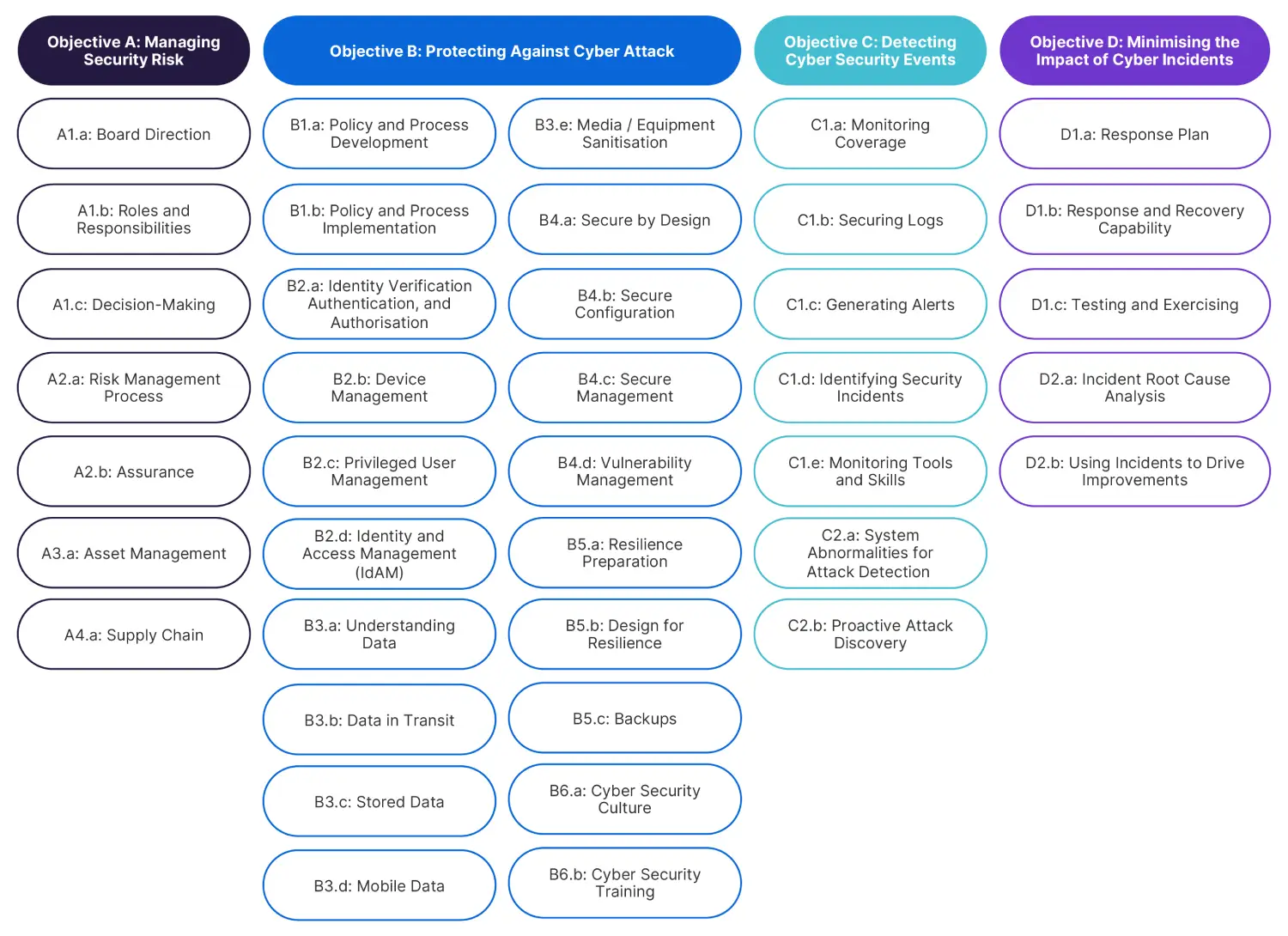
An example which demonstrates this breakdown is Principle B2: Identity and Access Control, which is one of the six elements of Objective B: Protecting Against Cyber Attack.
Below is a summary diagram of all Principles in version 3.1 of the CAF, mapped to the four overarching Objectives:
The 39 CAF Contributing Outcomes
Each Principle is supported by one or more Contributing Outcomes, of which there are 39 in total. These are lower-level groupings of the requirements of each Principle, each containing a collection of related IGPs, which represent the most granular level of the CAF.
Below is a summary diagram of all Contributing Outcomes in version 3.1 of the CAF, mapped to the four overarching Objectives:
Contributing Outcomes are assessed as either Not Achieved, Partially Achieved, or Achieved. Typically, an organisation will be expected to attain a defined mix of Not Achieved, Partially Achieved, and/or Achieved Contributing Outcomes through a CAF Profile. For a Principle to be met, each individual Contributing Outcome within that Principle must meet the requirements established in the relevant CAF Profile.
Further information on CAF Profiles is provided below.
The Role of Indicators of Good Practice (IGPs)
Each Contributing Outcome is supported by a series of IGPs, of which there are 443 in total. These are the granular requirements against which organisations are assessed. In accordance with the scoring mechanism outlined earlier, IGPs within a given Contributing Outcome are grouped into Not Achieved, Partially Achieved, and Achieved.
In general, Not Achieved IGPs are negative statements which reflect the absence of a control; Partially Achieved IGPs are positive but caveated security statements, and Achieved IGPs are fully positive security statements. Therefore, an assessment seeks to validate that Not Achieved IGPs are not true and that Partially Achieved or Achieved IGPs are true.
To illustrate this distinction look at the IGPs below, which have been drawn from Contributing Outcome B2.a (Identity Verification, Authentication and Authorisation):
(Not Achieved) “The number of authorised users and systems that have access to your networks and information systems are not limited to the minimum necessary.
(Partially Achieved) The number of authorised users and systems that have access to essential function networks and information systems is limited to the minimum necessary.
(Achieved) The number of authorised users and systems that have access to all your networks and information systems supporting the essential function is limited to the minimum necessary.
The Not Achieved indicator is clear bad practice. The Partially Achieved indicator demonstrates that some appropriate measures have been implemented, but that these only apply to systems that have access to essential function networks and information systems. The Achieved indicator represents the highest level of maturity, with appropriate controls having been implemented for all relevant network and information systems.
If a single Not Achieved IGP is true, the relevant Contributing Outcome as a whole is evaluated as Not Achieved (as there is bad practice evident). However, to meet the Partially Achieved or Achieved level, all Partially Achieved or Achieved IGPs supporting the Contributing Outcome must be true, with all Not Achieved IGPs being not true (meaning only good practice is evident).
While this approach has the advantage of giving a relatively granular set of requirements, there is a risk that it can lead to a ‘tick box’ mentality. The NCSC explicitly discourages this approach. While the CAF is a useful benchmark, every environment is different and assessments against the CAF need to be conducted intelligently. For example, it may be impossible to apply multi-factor authentication to some Operational Technology, but other compensating controls (such as physical access controls, secure remote access mechanisms, security monitoring, network segmentation etc.) might achieve a similar impact and meet the overall spirit of the Contributing Outcome.
Ultimately, when it comes to assessing against Contributing Outcomes, the NCSC encourages organisations to exercise expert judgement and to leverage cyber security experience. However, the IGPs should be seen as the primary building block against which organisations are in the main assessing themselves against.
Competent Authorities and the CAF
In principle, there is no specific legal requirement for Competent Authorities to use the CAF to assess compliance with the NIS Regulations – a Competent Authority could decide to base their assessments on another framework (such as the National Institute of Standards and Technology’s Cyber Security Framework [NIST CSF]), or invent a brand new one from scratch. In practice, the majority of Competent Authorities have either already fully aligned themselves to the CAF, or are in the process of doing so, and the Government is committed to applying the CAF as widely as possible.
However, as outlined above, the CAF is an outcome-focussed framework which leaves significant room for interpretation when it is applied. Different Competent Authorities may have different thresholds for accepting that a particular Contributing Outcome or IGP has been met, reflecting different operating environments or threat profiles within the sectors they are responsible for.
Some Competent Authorities have also chosen to modify or extend the CAF to reflect these sector-specific features. Examples include the Civil Aviation Authority’s “CAF for Aviation” and Ofgem’s work to introduce a brand-new Objective E, relating to physical security and non-malicious hazards. Both of their frameworks are based on the CAF, but introduce subtle distinctions that operators of essential services (OES) in these sectors need to understand in order to meet their regulatory obligations.
CAF Profiles
Meeting the Achieved level for each of the 39 Contributing Outcomes requires a degree of maturity, capability, and investment which may not be feasible or proportionate for all OES or for all systems supporting a given essential function. For instance, the consequences of a cyber incident affecting a small electricity distributor may be dramatically different to a cyber incident that affects the UK electrical transmission network. Likewise, different sectors and OES may face different threats. Meeting the ‘Achieved’ level may also require considerable investments in time or money, the results of which may take several years to materialise and which may be difficult for Competent Authorities to assure.
To reflect these distinctions, the CAF includes the concept of ‘Profiles’. A Profile is essentially a Competent Authority’s statement of what level of performance or maturity an organisation needs to achieve in order to meet its regulatory requirements under the NIS Regulations. Typically, Competent Authorities issue a Baseline Profile (BP) and an Enhanced Profile (EP). As the names suggest, the Enhanced Profiles have more stringent requirements – for example, the target state of a Contributing Outcome under BP may only be Partially Achieved, but under EP be fully Achieved.
Through a careful use of Baseline and Enhanced Profiles, Competent Authorities can drive improvements in cyber security maturity, while ensuring that OES are investing their time and resources in the most impactful and efficient way.
If you are an OES and in any doubt over the assessment mechanism or Profile which you are required to achieve, you should engage with your Competent Authority directly to clarify this.
Who Should Use the CAF?
The NCSC states that “outside of government, the organisations likely to find the CAF collection most useful fall into three broad categories”. These are:
Organisations within the UK Critical National Infrastructure (CNI).
Organisations subject to Network and Information Systems (NIS) Regulations.
Organisations managing cyber-related risks to public safety.
As such, the CAF was developed principally to support OES and their Competent Authorities. However, it is also increasingly being used by non-regulated organisations across the private sector. These include organisations which are not currently within the scope of the NIS Regulations but who may potentially be within the future, and also non-CNI organisations seeking an outcome-orientated framework to drive their cyber security program.
Any organisation can also set itself Profiles for different stages of their journey. For example, an organisation could create 2-year, 3-year, and 5-year Profiles to measure the progress of its cyber transformation program.
Supporting this, organisations can define their own essential functions (i.e. what is most important to you as a business) and use the CAF to assess if they are sufficiently protected at each stage of your maturity journey, relative to their value to you as an organisation and your customers.





